Serverless functions such as AWS Lambda, Google Cloud Functions and Azure Functions are increasingly popular among DevOps teams, as these cloud-based systems allow developers to build and run applications without managing the underlying infrastructure. But for all their benefits, serverless functions can also raise cybersecurity risk.
Thankfully, no matter which cloud service provider you’re using to build serverless applications, CrowdStrike has you covered with pre-runtime vulnerability assessment capabilities for AWS Lambda, Google Cloud Functions and Azure Functions due to a new integration between CrowdStrike Falcon® Cloud Security and CrowdStrike Falcon® Exposure Management.
Let’s explore how this new innovation delivered from the AI-native CrowdStrike Falcon® cybersecurity platform increases security coverage for cloud environments while increasing DevOps delivery speed as well.
Cybersecurity Challenges with Serverless Functions
Organizations that run serverless functions face three main cybersecurity challenges:
1. Poor visibility
Serverless functions are ephemeral, making it hard to get real-time visibility into serverless asset inventory and associated vulnerabilities. Plus, there’s no visibility into which serverless vulnerabilities have the highest potential impact and thus should be prioritized — increasing the risk of a breach.
2. Larger attack surface
With serverless functions, the cloud service provider is responsible for availability, and the developer is responsible for ensuring the confidentiality and integrity of the data processed by their functions. Serverless functions are event-driven and mainly run by responding to external inputs — the more inputs and events there are to respond to, the larger the attack surface, since each opportunity for input is a possible entry point for an attacker. For example, if an eCommerce application uses serverless functions to send notifications to customers every time an order is confirmed, an attacker can manipulate order confirmation input to send harmful links in the notifications.
Additionally, developers are responsible for writing the applications that run on serverless functions and ensuring proper configurations for the resources. This also widens the attack surface, as each serverless function has its own roles and permissions. If a function is misconfigured and overprivileged, it can lead to a threat actor getting access to an entire system.
3. Developers overwhelmed by vulnerability noise
There’s also the challenge of balancing a high number of vulnerabilities with tight deadlines for new innovations. As it stands today, teams are prioritizing vulnerabilities manually based on a primitive CVSS score, regardless of their exposure in production or business impact. This tends to delay vulnerability fixes or cause teams to focus on the wrong ones first.
New Serverless Protections in Falcon Cloud Security
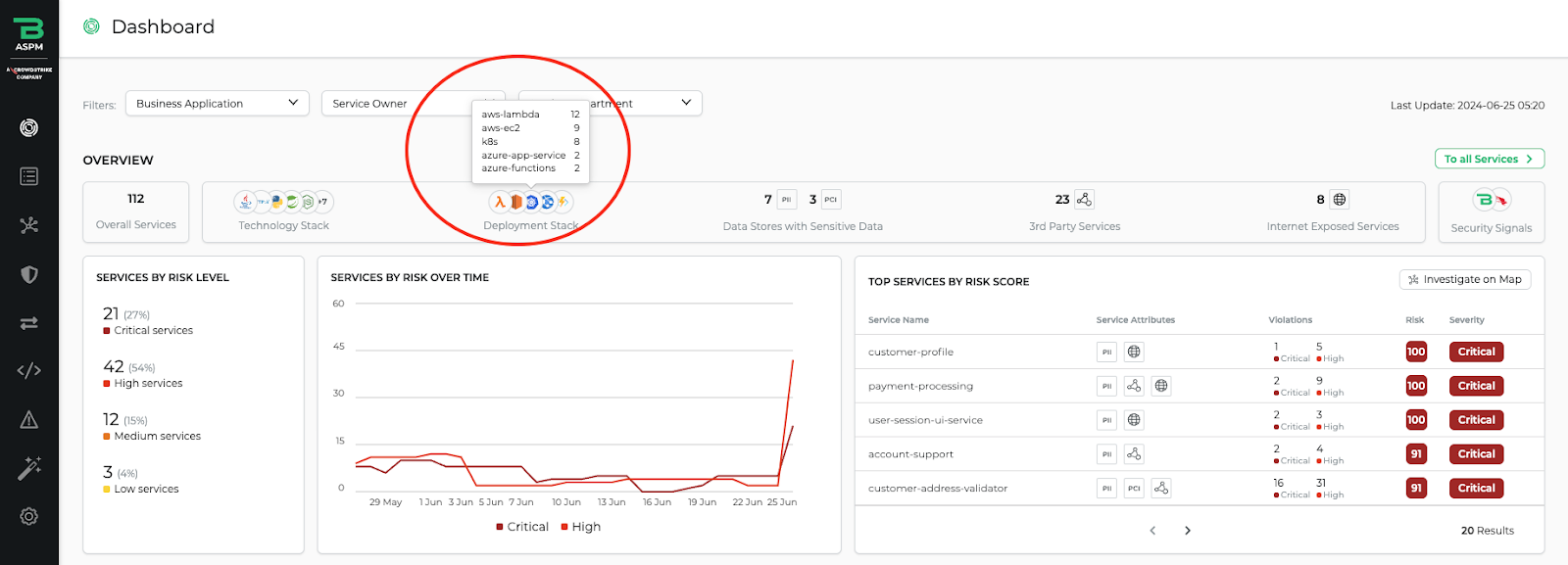
CrowdStrike Falcon® Cloud Security has long offered pre-runtime vulnerability assessment for cloud workloads across AWS, Google Cloud and Azure. Now, protection has been extended across their corresponding serverless functions as well. With these serverless protections — included with Falcon Cloud Security for Containers — CrowdStrike provides complete visibility into all cloud threats, vulnerabilities and attack surfaces, making it easy for DevOps and security teams to align on which security vulnerabilities to focus on first so they can innovate quickly.
Better Visibility
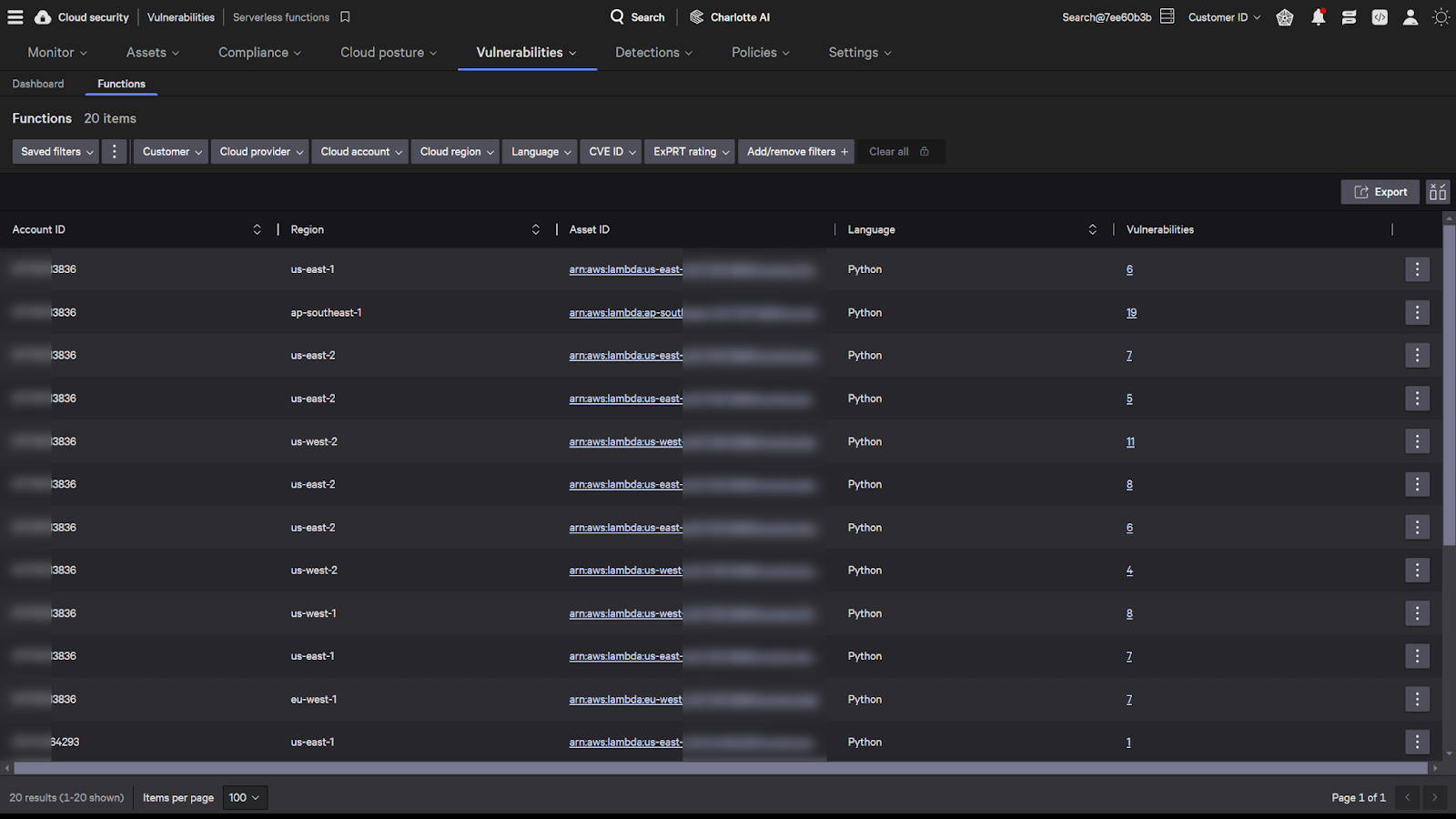
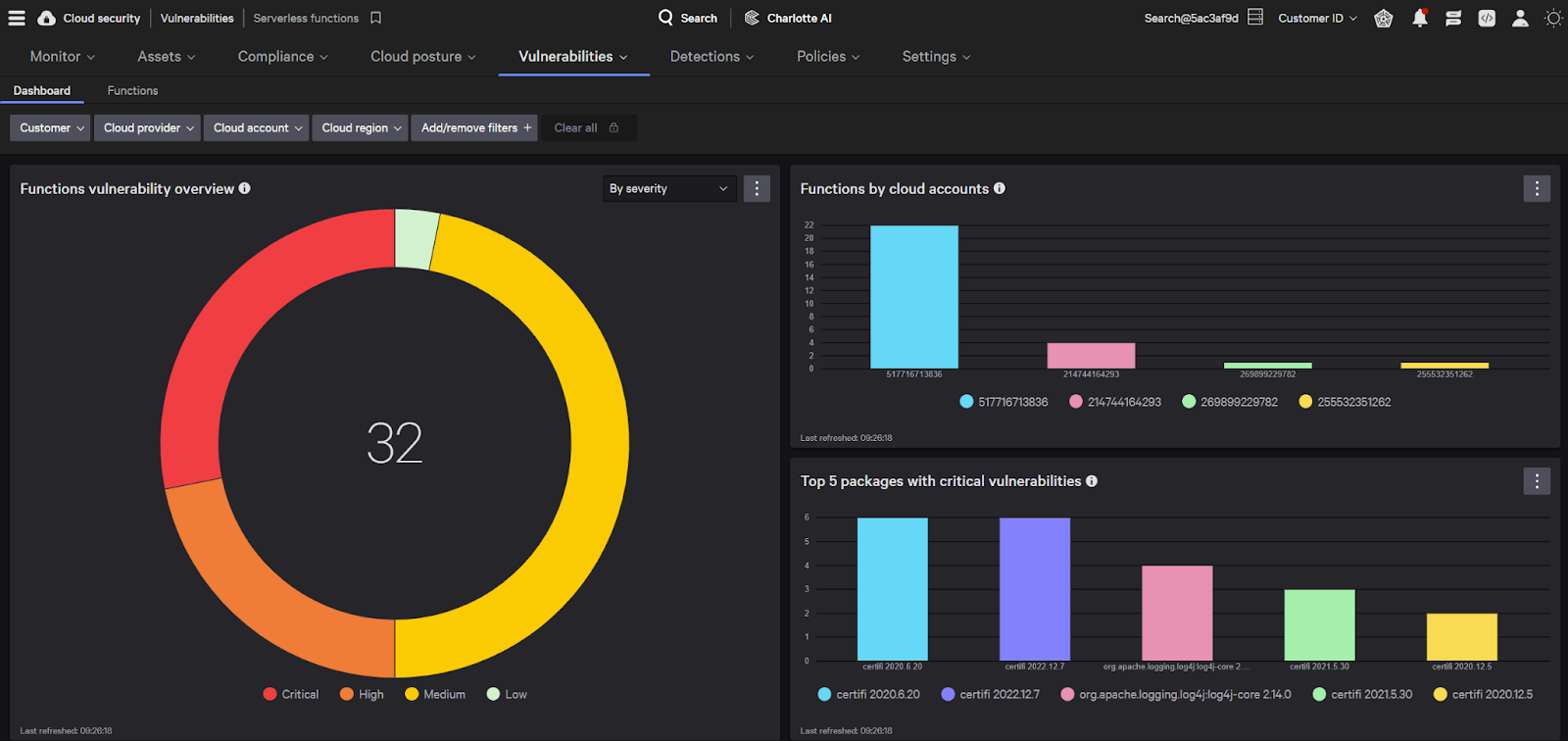
A key component of serverless security is having a complete inventory of functions in your environment. Falcon Cloud Security uses cloud account registrations to discover serverless functions in cloud service provider accounts and all package dependencies. Any assets discovered will appear in the functions details page to show all packages and any associated vulnerabilities — centralizing serverless security data into a single tool, no matter which cloud providers, languages or runtimes are being used.
And, CrowdStrike Falcon® Application Security Posture Management (ASPM) includes connectors for serverless functions, providing a complete posture assessment for everything that gets deployed into production. With this, customers can monitor their serverless security posture from pre-deployment to runtime, all with a single tool.
Pre-Runtime Assessments
Falcon Cloud Security runs pre-runtime assessments of function layers in your environment across all of the major cloud providers. Before serverless code is deployed, the scans proactively check for points of vulnerability, over-provisioned permissions and misconfigurations to reduce your risk of attack.
AI-Powered Vulnerability Prioritization
Core to these serverless innovations is our proprietary ExPRT.AI rating system, a predictive, dynamic, AI-powered rating model that prioritizes vulnerabilities based on the risk they pose to your environment. ExPRT.AI incorporates exploit status and advanced threat intelligence provided by CrowdStrike’s industry-leading intelligence and threat hunting team. Instead of relying on generic CVSS scores or navigating long vulnerability reports, teams can prioritize risk based on business context and impact.
Bridging Security and DevOps
With Falcon Cloud Security, CrowdStrike takes a unique, risk-based approach to serverless vulnerability management, providing coverage across the software development life cycle with runtime coverage as well. This ensures protection from code to cloud against zero-days, missed vulnerabilities and other cloud-based attacks.
Cloud security is inherently complex, especially for emerging cloud technologies like serverless functions, which require strong collaboration between security and DevOps teams. These new protections from CrowdStrike strengthen the bridge between security and DevOps, allowing teams to innovate fast while keeping their serverless environments secure.
Additional Resources
- Read the blog, “Falcon Cloud Security Supports Google Cloud Run to Strengthen Serverless Application Security.”
- Schedule a free Cloud Security Health Check to visualize misconfigurations and other vulnerabilities in minutes.
- Visit the Falcon Cloud Security product page.
- Check out our Complete Guide to CNAPPs.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)