At CrowdStrike, we’ve long known how difficult it is to detect attacks that involve stolen credentials. We themed the CrowdStrike 2024 Global Threat Report “the year of stealth” to highlight how attackers are moving away from malware and malicious attachments and toward more subtle and effective methods such as credential phishing, password spraying and social engineering to accomplish their objectives.
The AI-native CrowdStrike Falcon® cybersecurity platform is the industry’s only platform that unifies identity protection and endpoint security to proactively stop hybrid identity-based threats through real-time prevention, behavioral baselining and more than 60 high-fidelity, first-party detections covering Active Directory, Okta, Entra, Ping and ADFS. However, some security teams also need third-party data — such as Okta logs to build their own detections — for SIEM use cases.
This blog shares how you can consolidate on the Falcon platform and transform your SOC with CrowdStrike Falcon® Next-Gen SIEM to further strengthen your defenses against identity-based attacks. Read on to learn why we’re offering 10GB/day of free third-party data ingestion from tools like Okta to jumpstart your next-gen SIEM journey.
Detect Identity-based Attacks with Falcon Next-Gen SIEM
Falcon Next-Gen SIEM lets you easily extend the power of the Falcon platform to third-party data sources. Many CrowdStrike customers already have endpoint and identity protection data in Falcon. Now customers can get visibility into third-party data like Okta logs with our robust ecosystem of data connectors and parsers, to provide a more complete picture of an attack.
Falcon Next-Gen SIEM easily ingests rich identity data to obtain user events such as logins, authentication attempts, MFA challenges and account lockouts. Out-of-the-box correlation rules also highlight particularly suspicious activity, such when an Okta admin role is assigned to a user or group.
Unlike legacy SIEMs saddled with low-fidelity, generic rules that require significant effort to tune, Falcon Next-Gen SIEM offers precise detections, carefully refined by industry-leading adversary research and record-setting MDR teams. Data can also be correlated with native Falcon data such as endpoint telemetry or used in custom rules built with a unified language for search, parsing and dashboards.
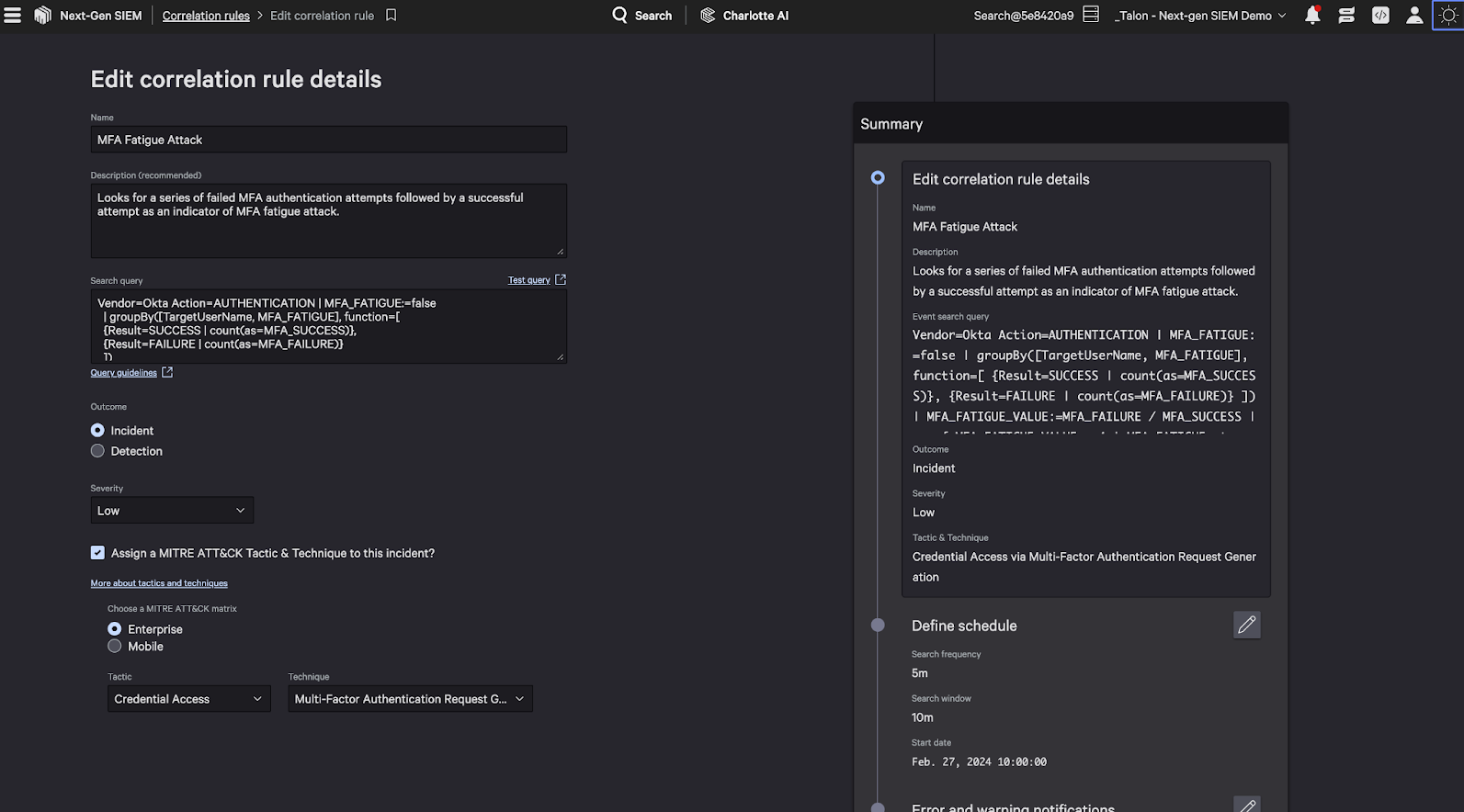
Figure 2. Easily build and tune Falcon Next-Gen SIEM correlation rules using the same common language across all third-party data.
In Falcon Next-Gen SIEM, you can view alert severity and group alerts into incidents to help prioritize triage and analysis efforts. The incident shown below has automatically been mapped to the MITRE ATT&CK® framework, showing an adversary is seeking to obtain user credentials with an MFA fatigue attack.
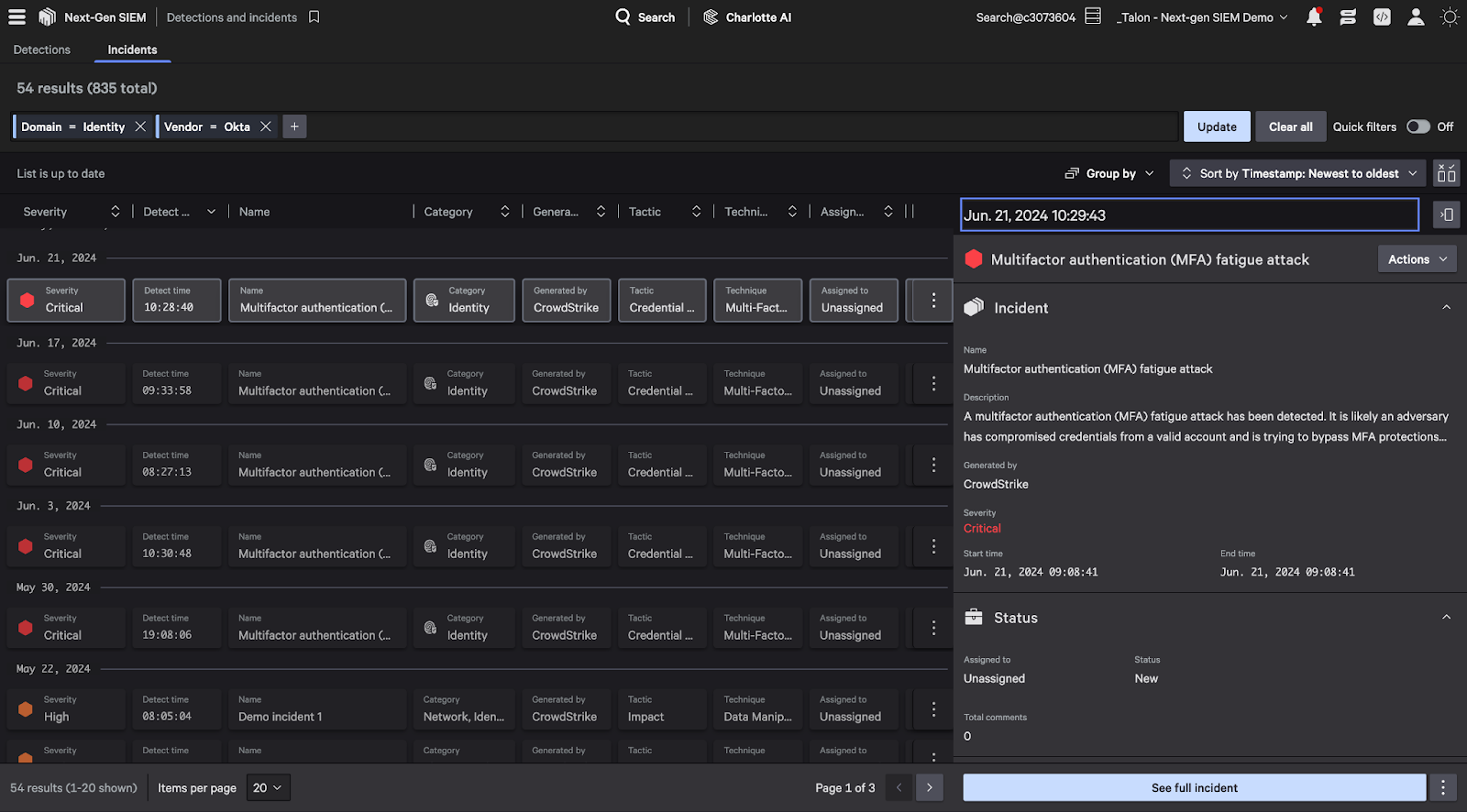
Figure 3. Falcon Next-Gen SIEM unifies alerts from all data sources with the ability to quickly sort and filter based on severity, source, MITRE technique and more.
Monitoring with Live Dashboards
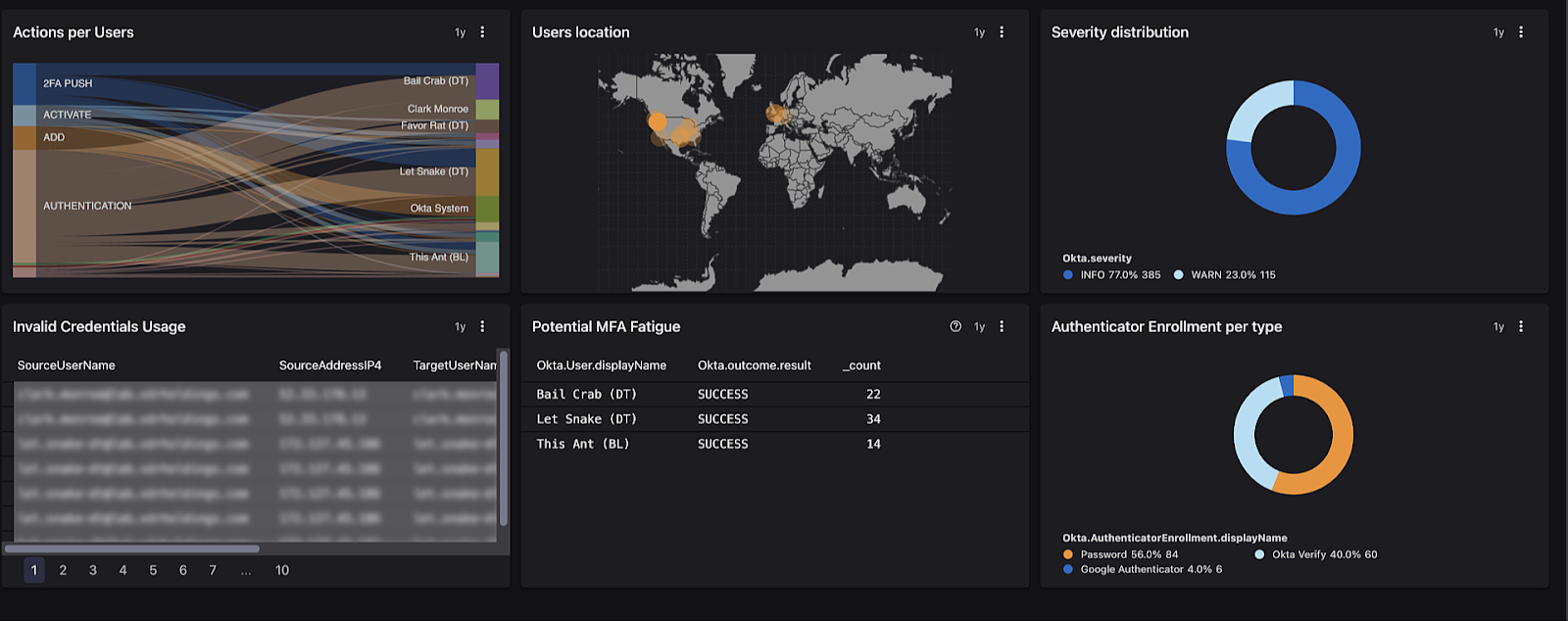
You can also use templates or create your own dashboards for easy reporting and real-time monitoring. For Okta data, you might be interested in understanding where, when and how often logins are happening to your different applications, as well as prompts for MFA challenges.
Investigate and Respond
With Falcon Next-Gen SIEM, you can seamlessly pivot to the Incident Workbench to easily view incident details in an elegant visual graph such as related hosts and processes. You can also leverage suggestions from Charlotte AI to further enrich the event, ensuring you have the full picture of an attack.
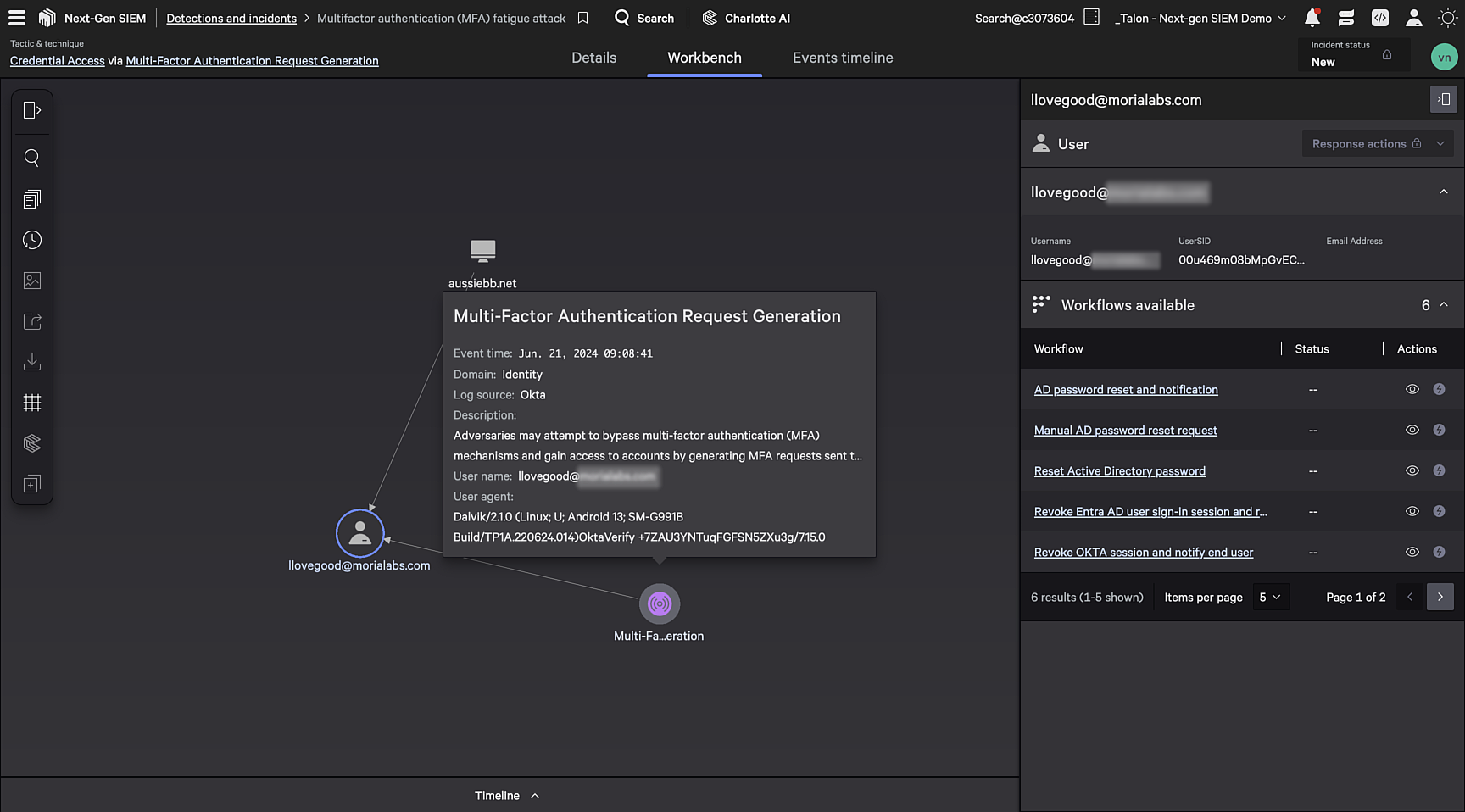
Figure 5. See the full scope of an incident, including hosts, identities and related processes in a single console with the Incident Workbench.
You can also easily view the raw log and event details with a single click, without needing to manually write additional queries.
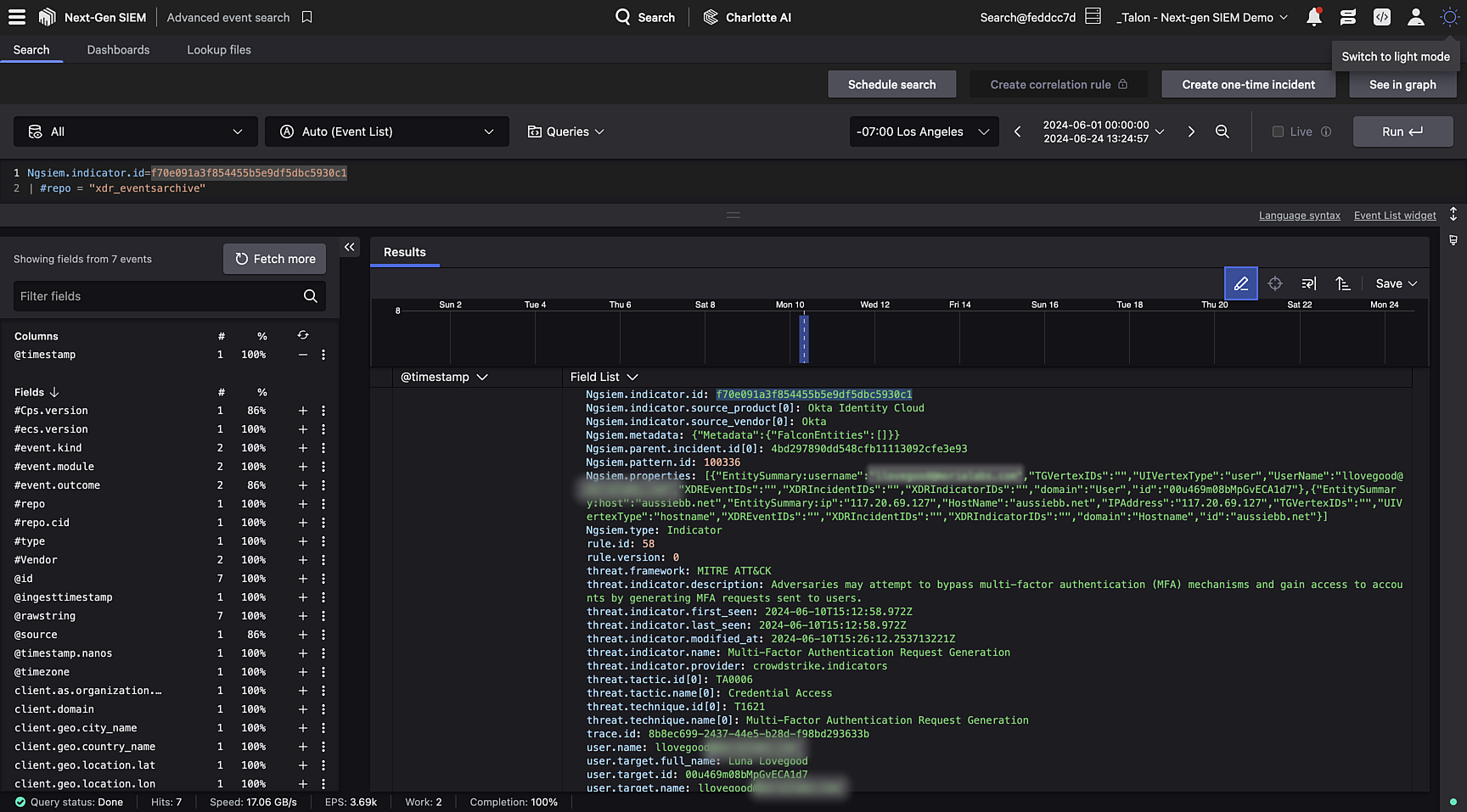
Figure 6. Advanced event search makes investigations lightning-fast and pain-free with a direct link from the incident to a pre-populated query.
To respond at machine speed, you can upgrade to a paid Falcon Next-Gen SIEM subscription and leverage automated workflows and apply policies that remediate the most common identity-based attacks, such as clearing session tokens in the event that a user’s session has been compromised. With Okta, you can also execute a playbook to automatically revoke access, reset MFA factors and force a password reset — a process that could take dozens of hours per week of analyst time if performed manually.
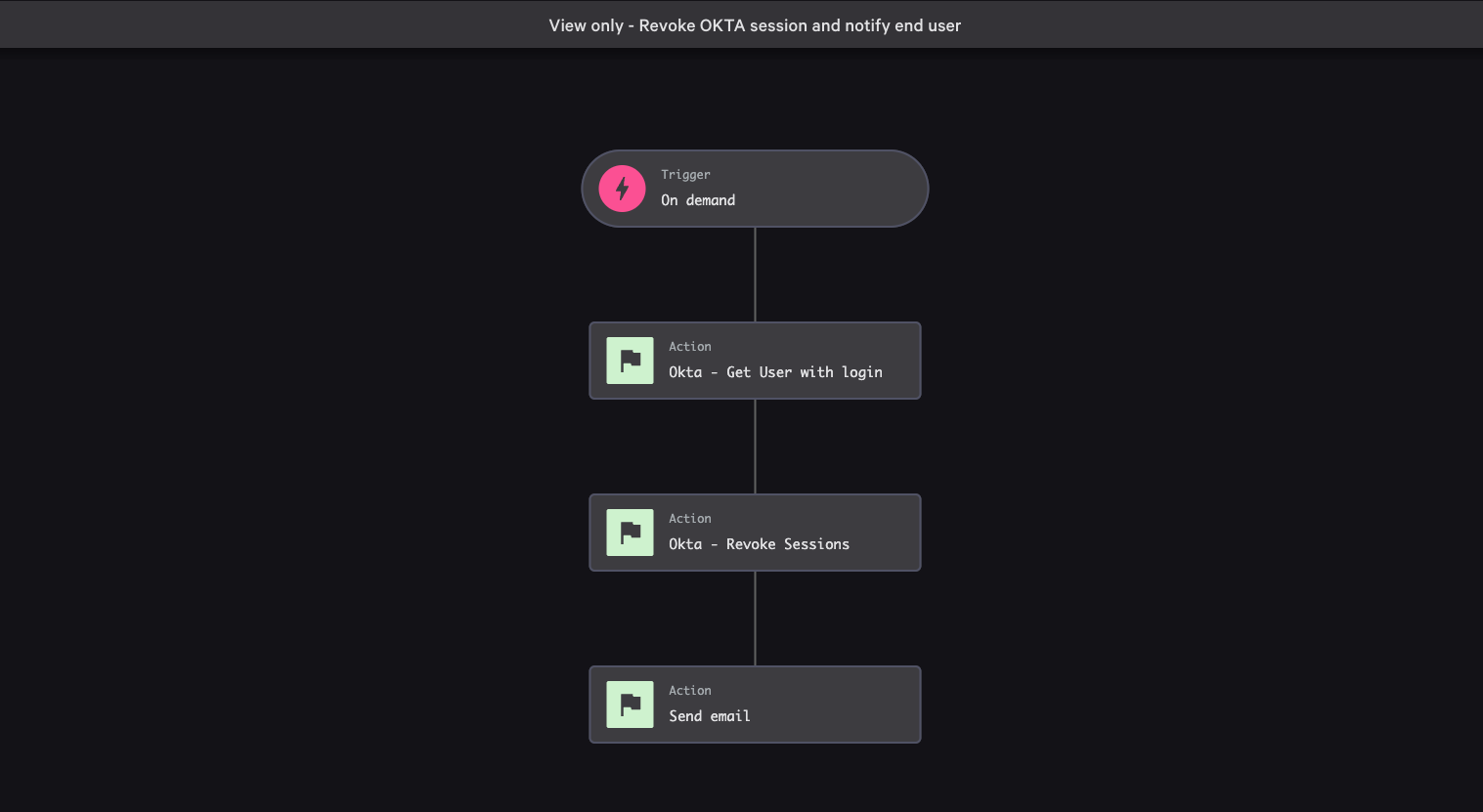
Figure 7. Falcon Fusion SOAR speeds up incident investigation and response with workflow automation and orchestration across the Falcon platform and third-party tools.
Transform Your SOC with Falcon Next-Gen SIEM and Identity Data
Start on your journey with Falcon Next-Gen SIEM and identity data like Okta logs today to unlock powerful detection, investigation and response capabilities. Existing customers of CrowdStrike Falcon® Insight XDR can ingest up to 10GB per day of third-party data at no additional cost. Make the most of this offer by ingesting high-value data, such as identity logs, into the Falcon platform to stop identity-based threats.
Contact your sales representative or technical account manager to learn more about this offering.
Additional Resources
- Read this technical blog to start ingesting third-party identity data into Falcon Next-Gen SIEM.
- Learn how to use 10GB of third-party ingestion for email data and phishing use cases.
- Learn about key benefits of next-gen SIEM in the Falcon Next-Gen SIEM data sheet.
- Sign up to attend our Next-Gen SIEM Showcase.
- Read the Complete Guide to Next-Gen SIEM to learn how to modernize your SOC.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)