With offense-focused methodologies being created around “living off the land” and “bring your own land,” we would like to cover a somewhat overlooked concept: “staying off the land.” This simple concept revolves around the idea of limiting the use of tooling used for offensive purposes executed on a compromised host. With endpoint detection and response (EDR) and other security products increasingly focused on looking for known malicious tooling and LOLbas, the simple approach of conducting activity off-host as much as possible can greatly reduce the attacker’s chance of being detected. This blog covers some common techniques and tooling that support this cyberattack methodology. The tactics, techniques and procedures (TTP) discussed focus primarily on an Active Directory (AD) environment.
Initial Access
In order to access a host remotely, an attacker needs to either introduce some form of malicious software or use the host’s existing software to initialize a command and control (C2) channel. Generally, this is in the form of a call-back mechanism such as a remote access trojan (RAT). Most RATs are malicious pieces of software delivered either as a standalone binary, shellcode or script, or a combination of these. The goal is to establish a channel between the attacker and victim for C2 communication. Most mature RATs provide the functionality required to create a SOCKS proxy on the compromised host and give the attacker access to this proxy over the established C2 channel. SOCKS proxies allow most network traffic to be tunneled over the proxy — commonly used to encapsulate TCP packets — and transfer them from one network to another. Once a RAT is in place and a SOCKS proxy is created, the attacker can use it to turn the compromised host into a “dumb pipe” into the victim’s network. This access allows the attacker to conduct the majority of their malicious activity without bringing additional tooling into a host. Compromised hosts simply act as pipes into a victim network, granting the attacker access to all resources within the network.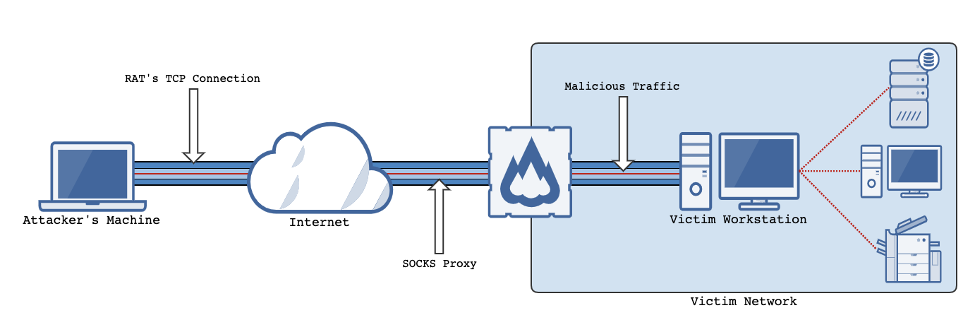
Discovery
Once an attacker has established a foothold, enumeration of the landscape begins. Common techniques for enumeration can be conducted from the attacker’s system instead of the compromised host. In order to direct the traffic within the victim’s network, tools such as ProxyChains can be used to force network traffic over a specific SOCKS proxy by linking an application via LD_PRELOAD. While this technique allows you to keep the majority of tooling off of a compromised host, there are still plenty of indicators for a security team to alert and hunt on. That's why it is important for an attacker following this methodology to be aware of overall operational security and potential indicators being created even from a network standpoint. For example, we have observed multiple security teams monitoring for protocols that include source host names of “kali” (a common Linux distribution used by attackers and “red team” security professionals) to easily detect an attack and score a quick win. BloodHound is a common tool of choice for AD enumeration. There is a Python version of the BloodHound collector that can be run with ProxyChains to collect most of the standard BloodHound data set including AD objects (users, groups, computers, etc.), local administrators, user sessions and more. Other common methods of enumeration that can be conducted from an attacker’s machine include SPN scanning to identify services without port scanning, file share enumeration to identify readable and/or writable file shares, and web service fingerprinting, to name a few.
Privilege Escalation
In the privilege escalation phase, attackers can use several tools to gain elevated permissions within an environment. UsingProxyChains to wrap tooling over the SOCKS proxy, attackers can use a variety of common tools to gain privileges, including:
- Kerberoasting: GetUserSPN
- ASReproasting: GetNPUsers
- NTLM relaying: NTLMRelayx
- Password spraying: Spray
- EternalBlue: MS17-010 POC
As you might notice, a large amount of the tooling mentioned comes from Impacket. Impacket is a comprehensive library with a large number of example tools that provide extensive offensive capability for all phases of attack.
Lateral Movement
After gaining enough privileges, attackers will often establish additional C2 channels on new hosts as backup, or move laterally to enumerate another host in the hope of collecting credentials or sensitive information required to achieve the overall objective. Most Windows hosts can be remotely accessed over SMB and RPC (including WMI), and less desirable protocols such as RDP (which may result in potential user interruption and forensic artifact creation). SMB’s file transfer protocol can be used to upload malicious files to a host or obtain sensitive data from a host. Tools such as Samba’s smbclient and Impacket’s smbclient allow attackers to pivot through one compromised host and upload or download files onto another host using valid credentials. RPC over the SMB protocol can be used to create scheduled tasks, resulting in command or code execution using tools like Impacket’s services. DCOM/WMI over RPC can also be used for command execution with tools including dcomexec and wmiexec. It should be noted that some of these tools have options or features that will create files on the remote host — however, this is counter-productive to staying off of the land. An example of this is wmiexec. WMI can be used to run commands on a remote host by calling the Win32_Process class. This class does not return the output of a command over WMI. Wmiexec allows you to view the output of a command by redirecting standard output to a file on disk and then pulling down that file over SMB to read the command output. This can be avoided by instructing wmiexec to be non-interactive. It is always important to have a full understanding of what a tool is doing “under the hood,” and full code reviews should be conducted on all tooling prior to use.
Attack Path Example
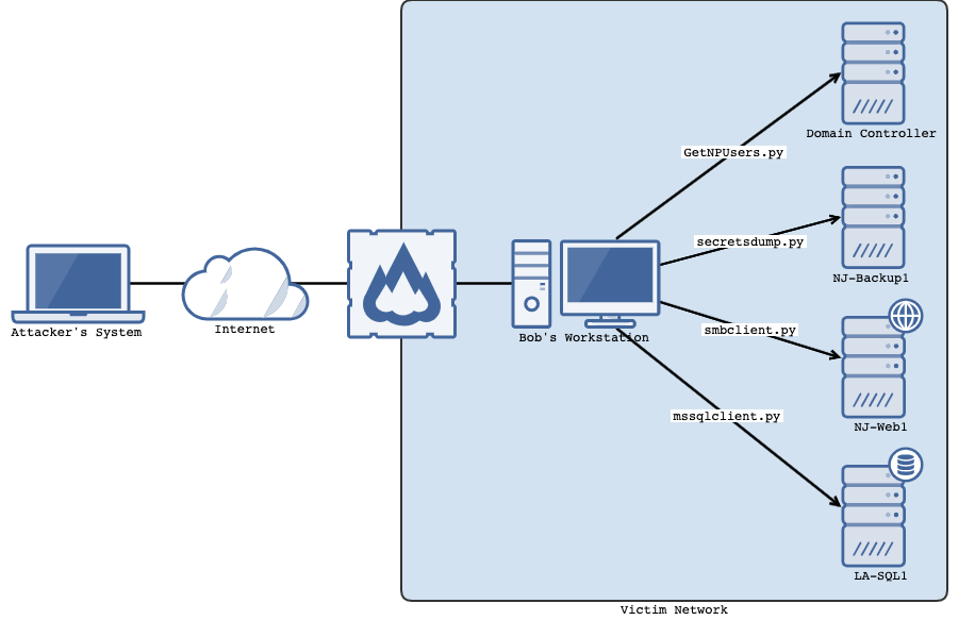
- The attacker successfully phishes a user named Bob by luring him to a fake log-in page for OneDrive where he signs in and downloads a malicious document.
- Upon opening the document, a CobaltStrike beacon is executed and a SOCKS proxy is created on Bob’s workstation.
- The attacker performs an ASReproasting attack against the domain controller using the credentials for Bob
obtained from the fake OneDrive login page:
proxychains GetNPUsers.py lab.local/bob -request -dc-ip $IPofDC -format hashcat -outputfile ASRepRoast.txt
- The attacker successfully cracks the service account credential for the bkp-adm account with hashcat:
hashcat -m 18200 ASRepRoast.txt -a 3 wordlist.txt
- The attacker runs the BloodHound collector to enumerate AD objects and finds that the bkp-adm user belongs to a NJ-Backup-Admins group:
proxychains bloodhound-python -d lab.local -u bkp-adm -c all -v --dns-tcp
- The attacker reviews BloodHound data, discovers a host named NJ-Backup1 and uses bkp-adm credentials to obtains local administrator’s NTLM hash (RID 500) from NJ-Backup1 (secretsdump.py will create temp files of registry hives on the host):
proxychains secretsdump.py lab.local/bkp-adm@nj-backup1
- The attacker reviews other hosts with “NJ-” prefix and discovers NJ-Web1
- The attacker successfully authenticates to NJ-Web1 with local administrator credentials obtained from NJ-Backup1:
proxychains smbclient.py -hashes :$LocalAdminHash ./administrator@nj-web1
- The attacker reviews the file system and finds a connection string containing credentials for an MS SQL user prod-dba on LA-QSL1 in c:\inetpub\wwwroot\web.config:
#From existing smbclient session use c$ get \inetpub\wwwroot\web.config
- The attacker uses the prod-dba SQL account to connect to the MS SQL instance on LA-SQL1 and enumerated databases:
proxychains mssqlclient.py prod-dba@la-sql1
- The attacker dumps the customer database and obtains a full list of client credit cards and personally identifiable information (PII):
Conclusion
As shown in the attack scenario above, an attacker can gain access to a single workstation in a victim network and with that access carry out a full attack, obtaining valuable assets. The attack path does not require an attacker to introduce malicious tooling or misuse existing binaries on a compromised host to reach their objective. This is not to say that this type of path could not be detected — in fact, many facets of this attack can be identified when looking for the proper indicators. The benefit of the “stay off the land” methodology is its reduction in potential indicators or alerts by avoiding conducting malicious activities on compromised hosts. This methodology may not be the best fit for every scenario, but it is an additional strategy in an attacker’s arsenal.
Additional Resources
- Learn more about how CrowdStrike can help your organization improve your cybersecurity readiness by visiting the CrowdStrike Services webpage.
- Read about CrowdStrike Red Team / Blue Team exercises by downloading the data sheet.
- Learn more about the powerful CrowdStrike Falcon® platform by visiting the webpage.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)











































