Threat hunting is the discipline of employing human analysts to actively search for and disrupt distinctly human threats. It leverages smart and creative defenders to identify the stealthy techniques that are purposefully designed by adversaries to evade our best algorithms and analytics. In many ways, threat hunting represents the last, best line of defense against modern threats.
Threat hunting, like most cybersecurity disciplines, requires balanced investment across three key pillars: technology, people and process. Optimizing the relationship between these pillars ensures measurable and repeatable results. Unfortunately, according to the SANS 2019 Threat Hunting Survey, organizations that threat hunt tend to place a stronger emphasis on investments in technology, with 71% indicating it is the first or second focus of their threat hunting resources. The authors of the white paper detailing the survey results say this “could be a costly mistake,” because technology spend may be less likely to result in finding and stopping adversaries than investments in staff, enablement, training and overall process. When done in an ad-hoc manner, threat hunting delivers ad-hoc results. This is a key reason that the survey found only 29% of organizations conducting threat hunting as a formal program with specifically assigned staff. When threat hunting follows a continuous, methodical process that accounts not only for uncovering threat activity, but making it actionable for incident responders, threat hunting becomes an indispensable weapon in the security operations center (SOC) arsenal.
Introducing OverWatch SEARCH Threat Hunting Methodology
The CrowdStrike® Falcon OverWatchTM team is one of the industry’s most sophisticated threat hunting teams, responsible for continuous hunting across a massive global data set. Key to the team’s success is OverWatch’s carefully tuned methodology, SEARCH, which supplies the framework needed to balance the people, process and technology, providing successful threat hunting results every minute of every day. In the following, we break down the components of the SEARCH methodology, detailing what is needed for a successful threat hunting program and outlining the keys to Falcon OverWatch’s success.
Sense
Threat hunting starts with collecting data. Broad and deep telemetry that captures a wide range of activity and behaviors gives hunters the pool of information that will serve as the foundation for the team’s threat hunting efforts.
The CrowdStrike Falcon®® lightweight agent provides the industry’s richest sets of endpoint telemetry, acting as a flight data recorder for endpoints and workloads. Every week, Falcon sensors stream more than three trillion events into CrowdStrike Threat Graph®, covering hundreds of distinct behaviors and millions of endpoints. Having this rich data set ensures that OverWatch threat hunters have the raw visibility they need to uncover adversary activity, wherever it might try to hide.
Enrich
Data alone is merely the starting point. Without context, having a massive pool of raw security data can be more of a hindrance than a help. Putting data in context enables hunters to extract insights from their data sets quickly and efficiently. CrowdStrike’s proprietary Threat Graph connects the dots for OverWatch by capturing relationships between individual data points in a highly efficient cloud-scale graph database. It also incorporates insights from CrowdStrike’s world-class threat intelligence team that supplies detailed, up-to-the-minute observations on the tradecraft of more than 140 adversary groups. Combining Threat Graph with their own proprietary tools ensures that the OverWatch team is enabled to execute hunts with unprecedented speed and efficiency.
Analyze
With the foundation in place, effective threat hunting can begin. Threat hunting involves diving into this enriched data, leveraging statistical methods combined with human intuition and experience to form and test hypotheses around where and how a determined attacker might gain a foothold. To do this effectively requires analysts who have the ability to think like a sophisticated attacker, and then simultaneously form ideas of how a defender might counter. In many ways it can be like playing chess against yourself. OverWatch employs elite analysts with more than 200 years of combined experience in this game. OverWatch analysts come from a diverse range of backgrounds, including law enforcement, military, government and commercial enterprise. Together, this team has the broad and deep expertise needed to uncover the faintest signs of adversary activity.
Reconstruct
Of course simply identifying a threat is not the final goal of threat hunting; a good deal of work remains in order to give a responder the information they need to take action. To understand the full scope of the intrusion, it must be reconstructed from the supporting data. Doing effective reconstruction requires threat hunters to ask themselves a series of questions (When did this start? How far did it spread? What damage was done? What users were involved?), and to get answers in real time. It also requires a system to gather and connect that data into a cohesive picture, stitching all the pieces of the intrusion together into a single attack narrative.
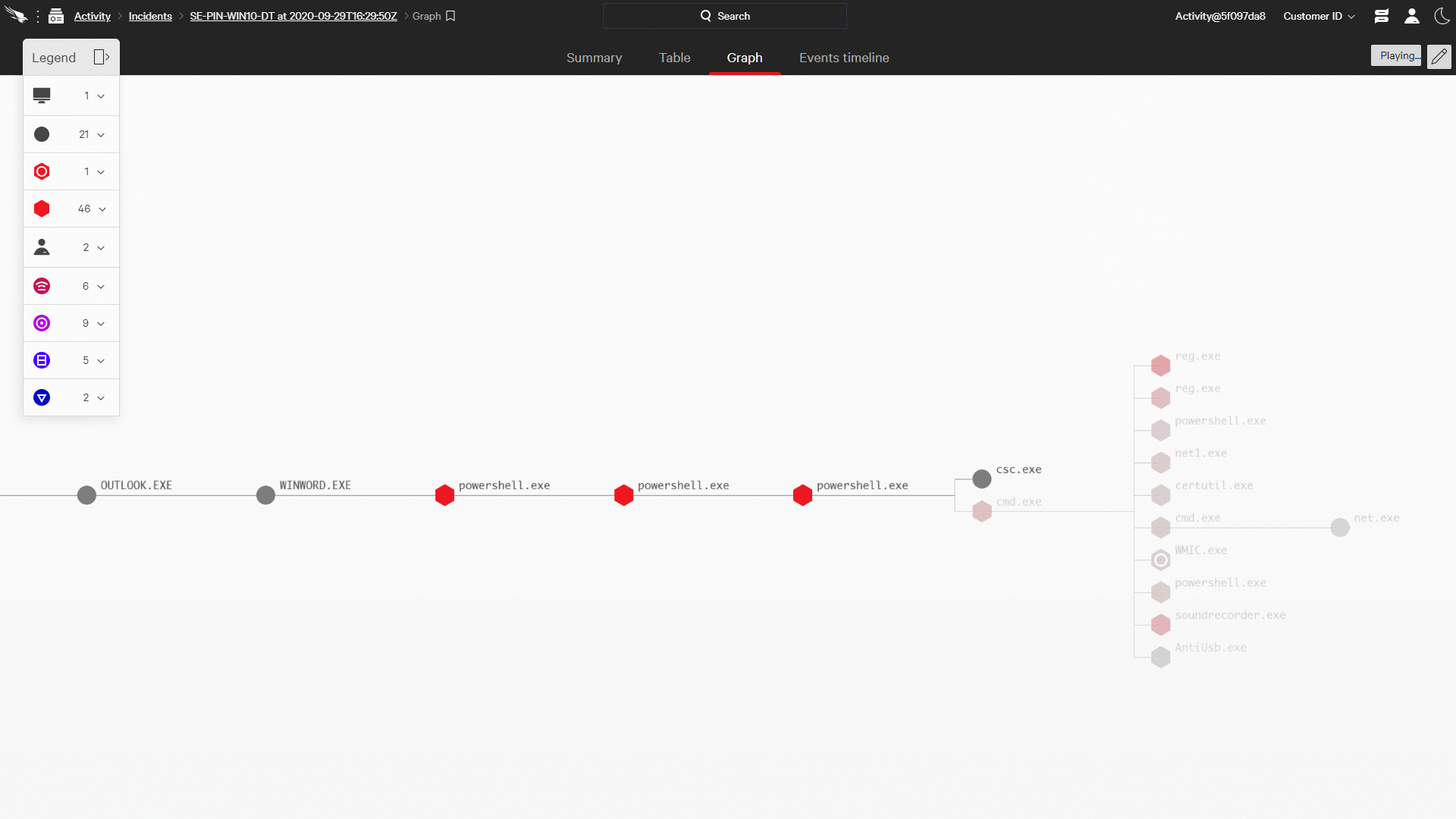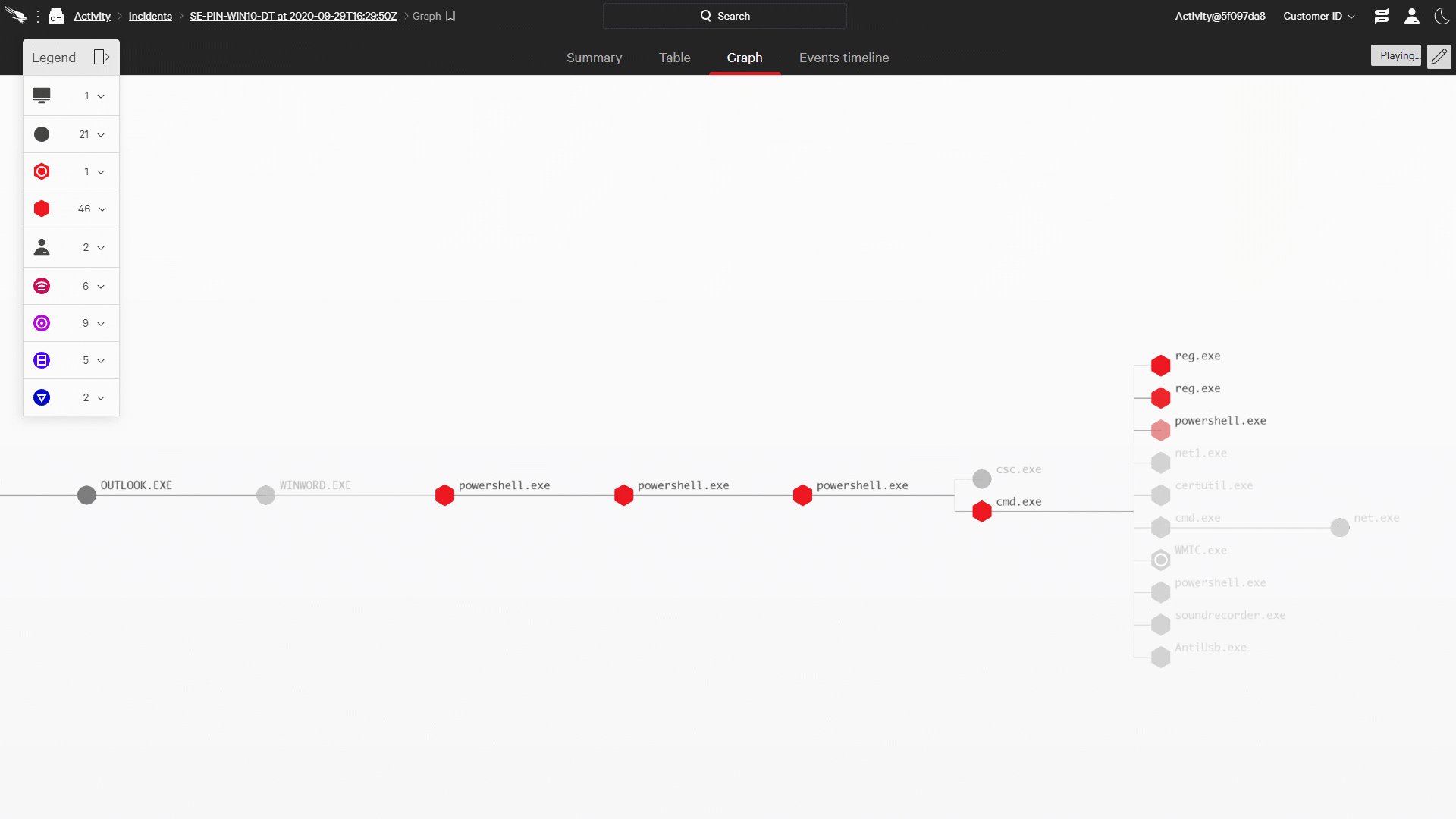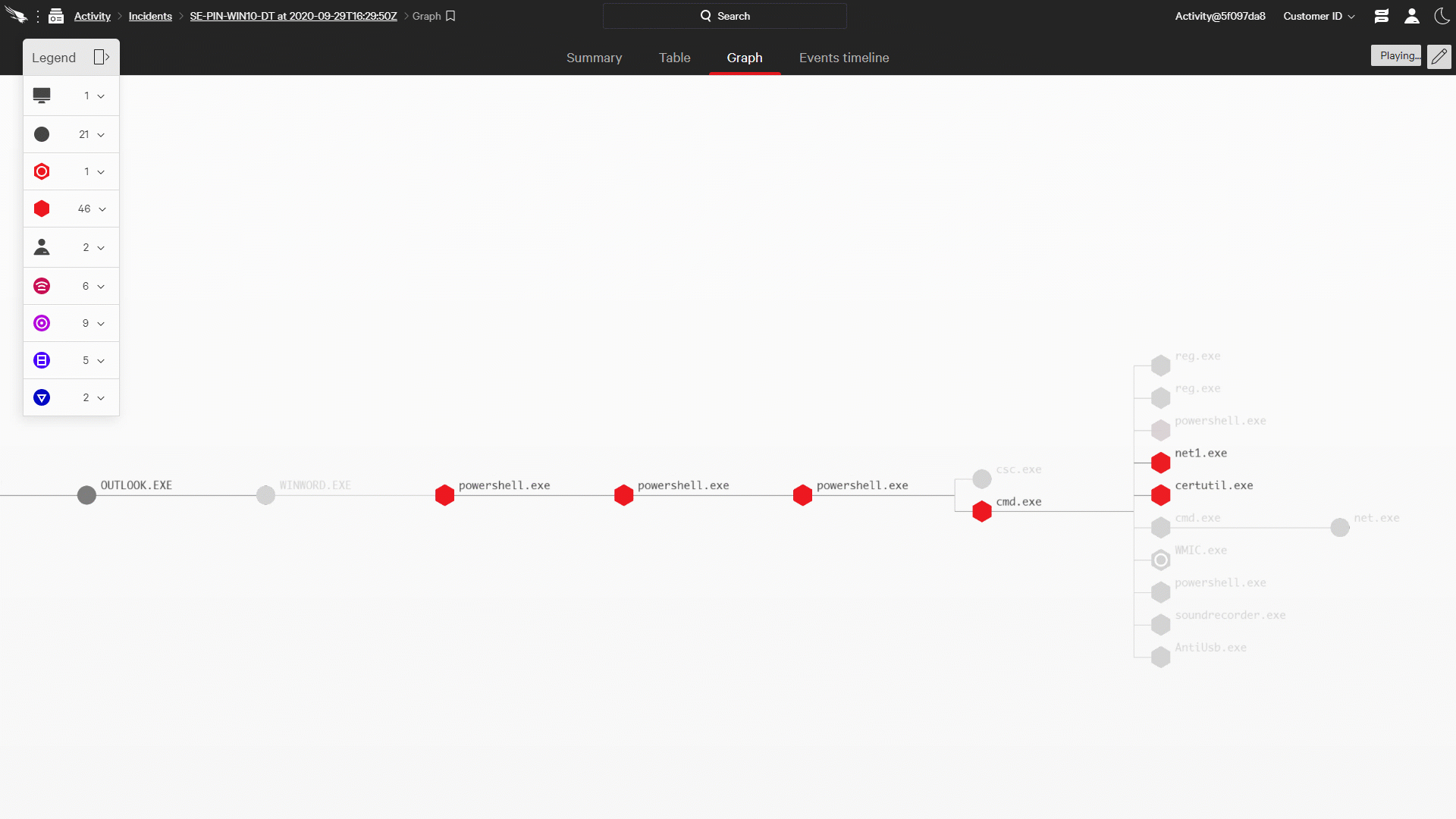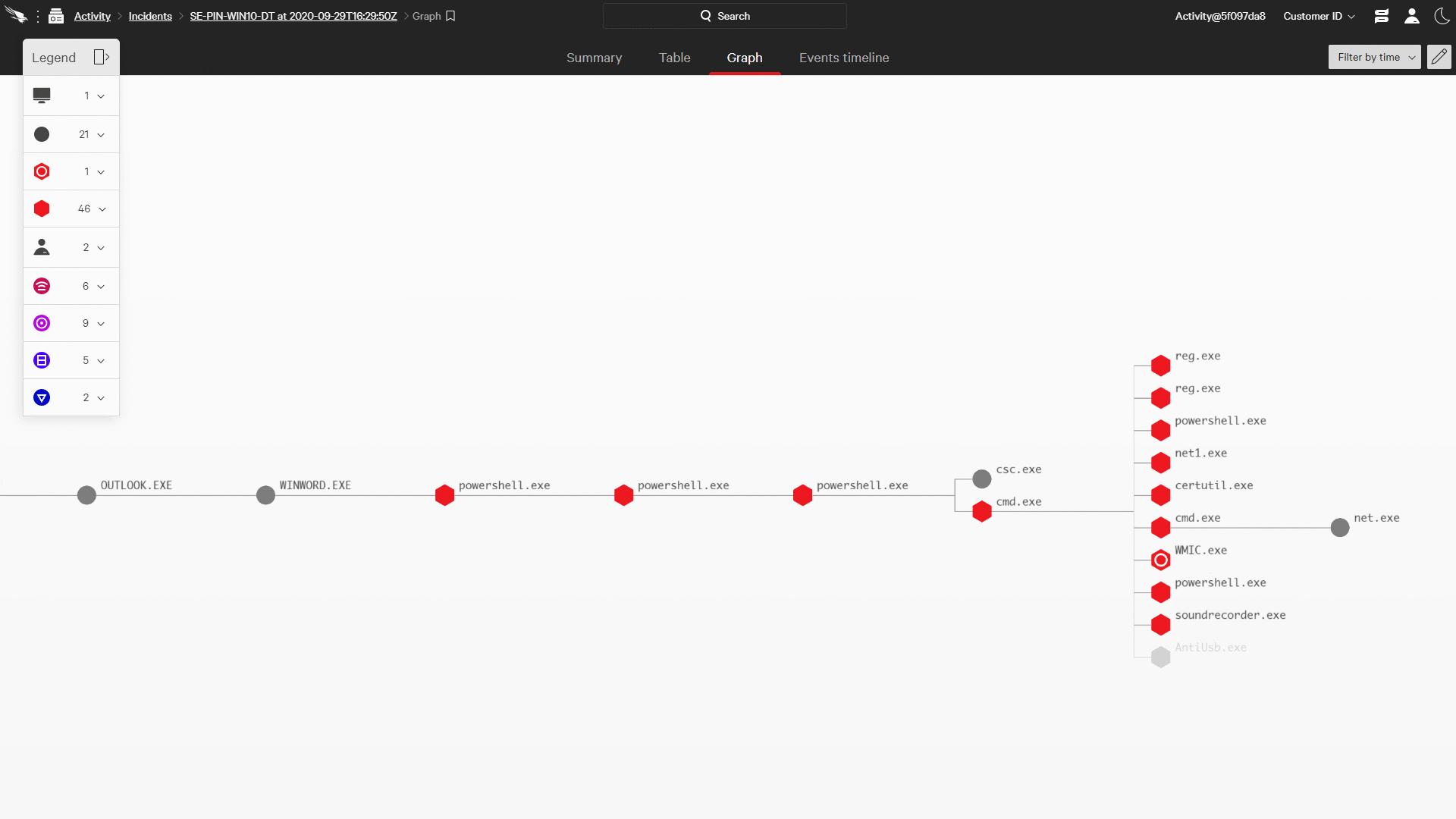 Figure 1: Falcon OverWatch Reconstructs Attacks in Near Real Time with the CrowdStrike Incident Workbench (click image to enlarge)
Figure 1: Falcon OverWatch Reconstructs Attacks in Near Real Time with the CrowdStrike Incident Workbench (click image to enlarge)The CrowdStrike Incident Workbench, a key feature of the Falcon platform, provides OverWatch with the ideal toolset to manage this process. OverWatch analysts leverage the power of the Threat Graph to get answers to their critical questions in seconds. The Incident Workbench provides the framework for the analyst to assemble the full story, and build out that story — as the intrusion progresses — in a manner that’s simple for a responder to digest and act upon.
Communicate
Once the scope of the intrusion is understood and documented, it’s time to take action. Generally speaking, the threat hunting team sounds the alarm on intrusions that need to be handled, but are not themselves responsible for the work of incident response. That work falls to others in the SOC, yet all this hard work is wasted if these individuals don’t get all the information and supporting context they need in time to act and prevent a breach.
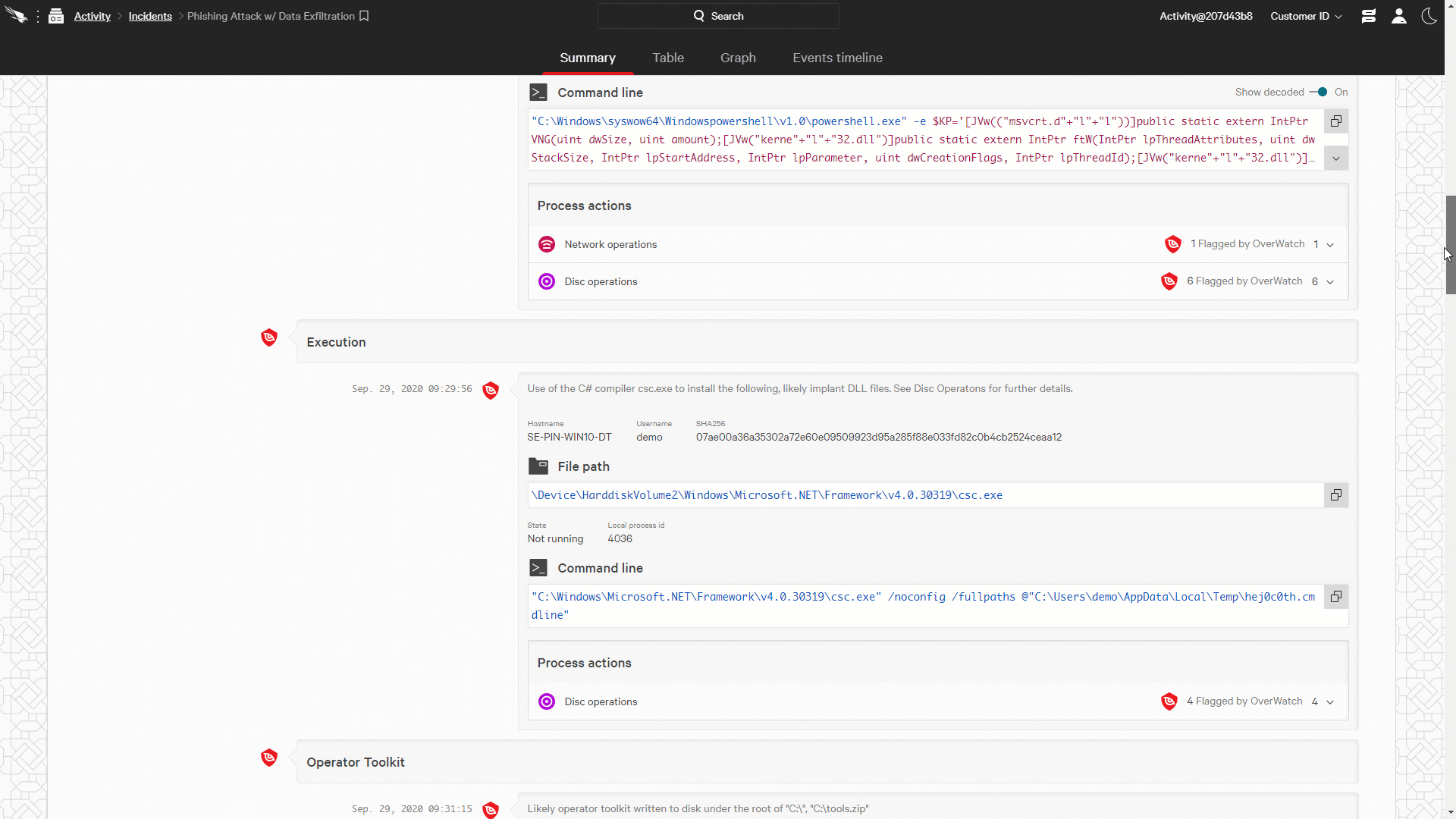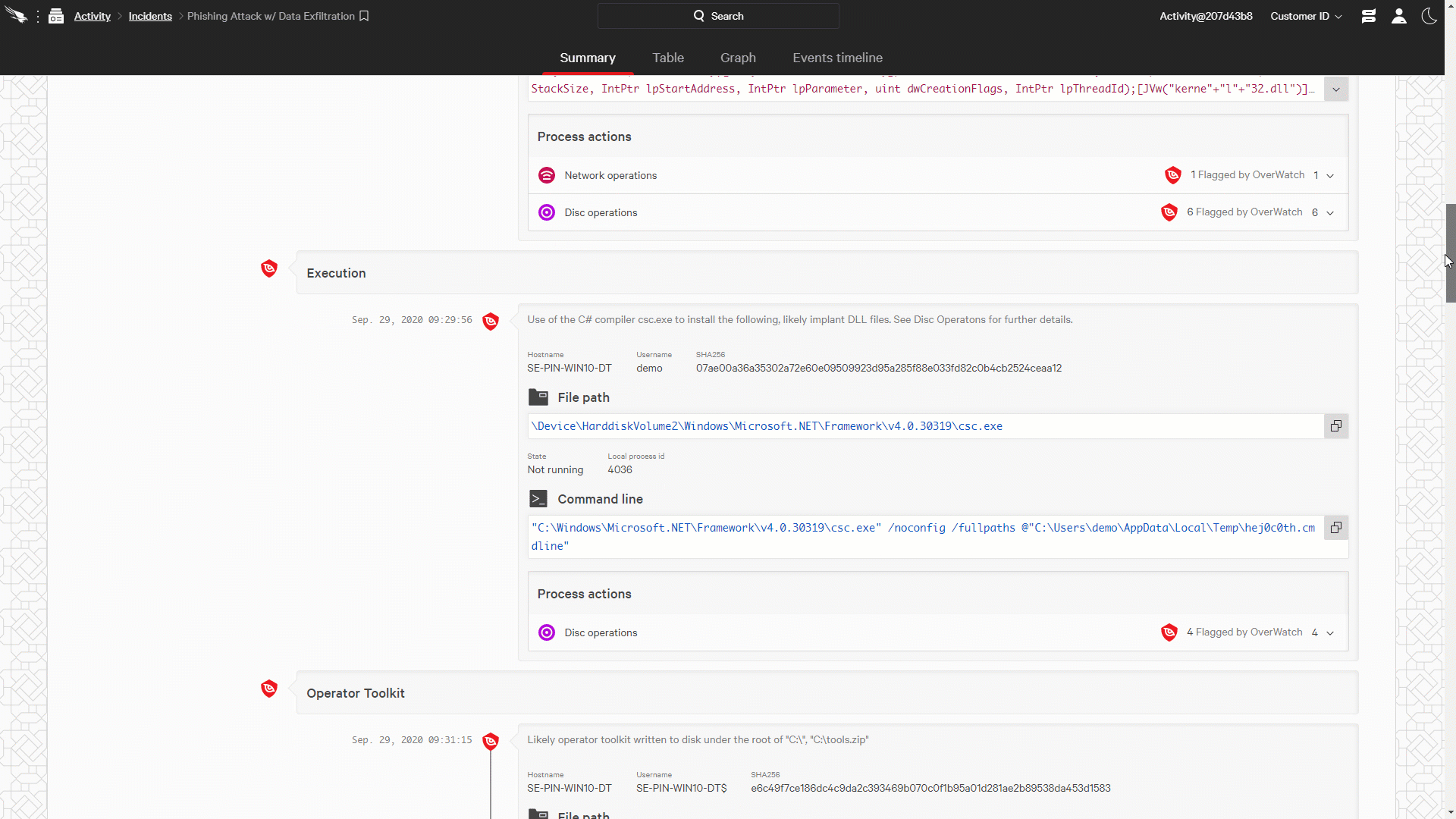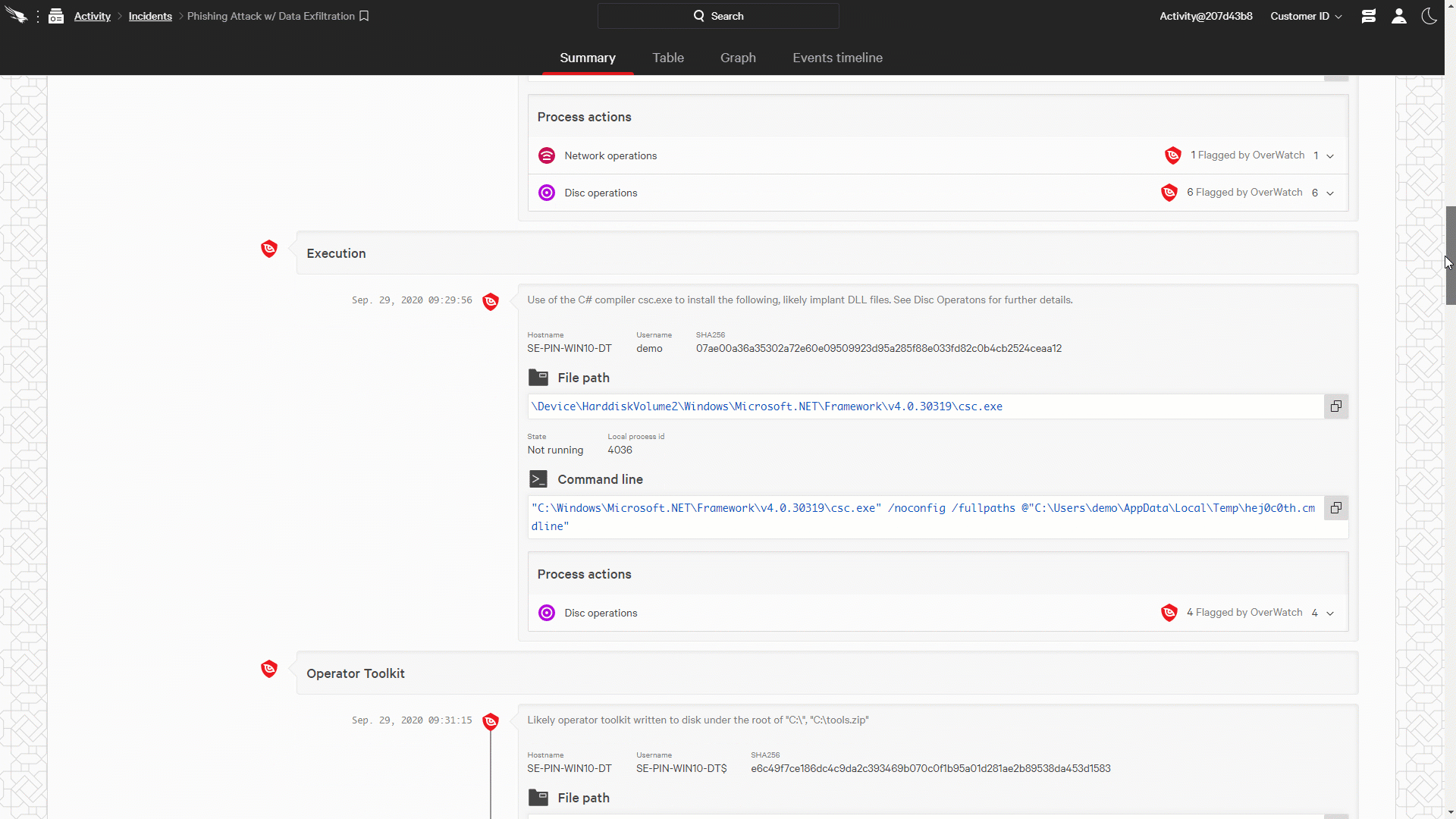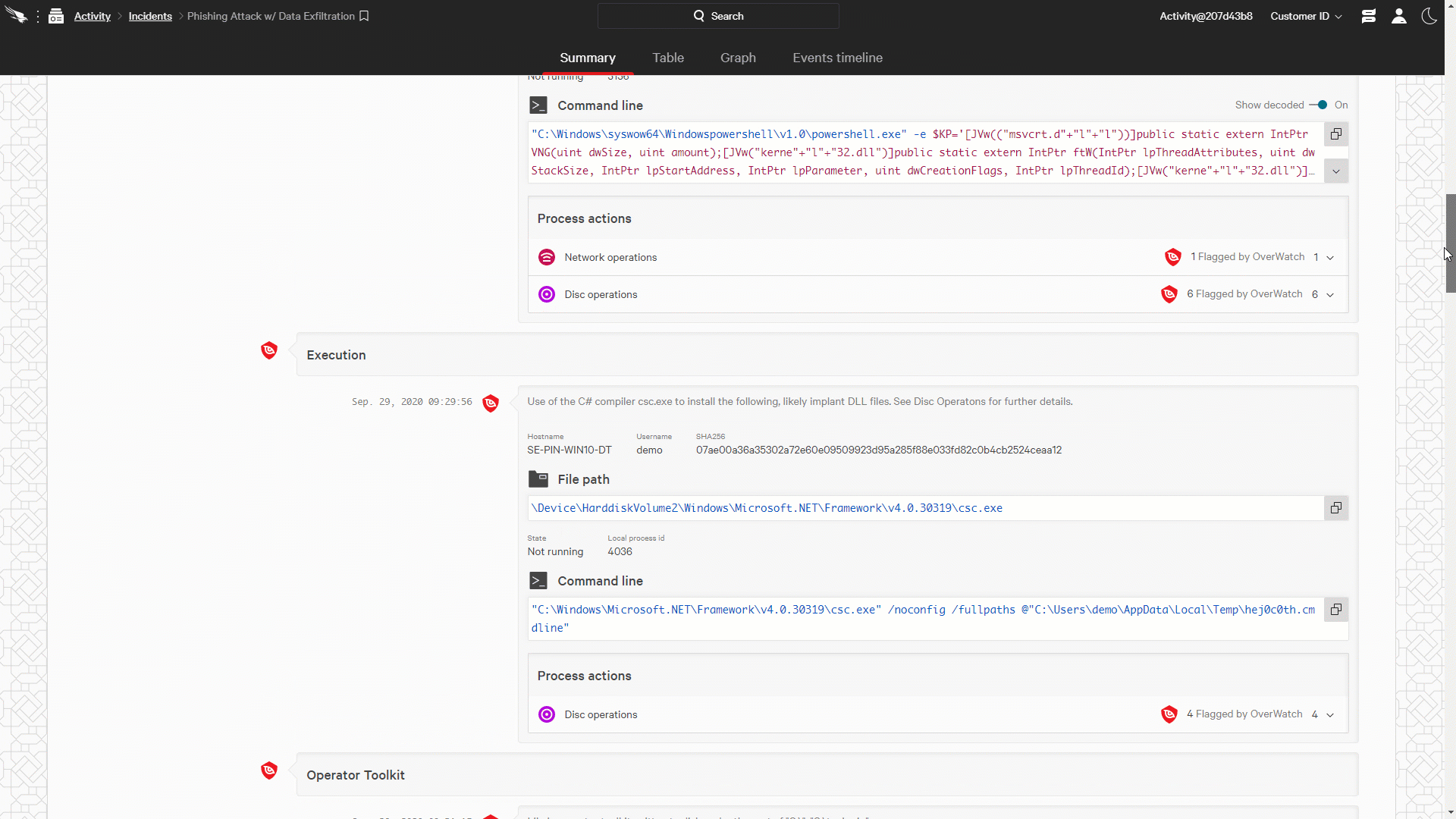 Figure 2: Falcon OverWatch Communicates Timely and Complete Intrusion Information through the Falcon Consol (click image to enlarge)
Figure 2: Falcon OverWatch Communicates Timely and Complete Intrusion Information through the Falcon Consol (click image to enlarge)The Falcon platform provides the perfect collaboration environment for threat hunters and organizations’ security teams. CrowdStrike pioneered the idea of creating a seamless union between the technology, our experts and your team, closing the gap between detection and response. As intrusions are identified and documented, OverWatch makes them available to responders via the Incident Workbench, empowering them with timely, complete information all within a single cloud-native console. See for yourself how Falcon OverWatch helps organizations understand and act against a sophisticated intrusion through the powerful Incident Workbench.
Hone
Smart organizations realize that every successful threat hunt represents an opportunity to learn and improve. New and novel TTPs that are discovered during threat hunts highlight areas where automated detection techniques can be improved to detect, and ideally prevent, intrusions more quickly and effectively. Hunts that took minutes may be streamlined to take seconds next time.
OverWatch’s threat hunting activities generate a continuous stream of new insights that CrowdStrike can leverage to stay in front of intruders. Not only do these insights drive OverWatch to develop new and innovative hunting techniques, but they also represent a rich source of new automated detection techniques for the Falcon platform, ensuring that CrowdStrike customers are always ready for the next new threat.
Conclusion
In the first half of 2020, the Falcon OverWatch team observed and interrupted more than 41,000 intrusion attempts for our customers all over the world. The SEARCH methodology shows how OverWatch optimizes the relationship between people, process and technology to deliver results every minute of every day, leaving the adversary nowhere to hide. Proactive human threat hunting remains a key component that is critical in CrowdStrike’s successful mission to stop breaches.
Additional Resources
- Download the 2020 OverWatch Threat Hunting Report.
- Visit the CrowdStrike Falcon® OverWatch webpage.
- See what SANS had to say in the SANS Review of OverWatch.
- Learn more about the powerful CrowdStrike Falcon® platform by visiting the product page.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and learn how true next-gen AV performs against today’s most sophisticated threats.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)











































