Consider this situation: A man talks on the phone with a known bank robber. He then rents a building next to a bank. Next, he buys duct tape and ski masks. Any one of these actions could be a red flag alerting police to a potential robbery. But together, they tell a more complete story of a crime in the making.
Similarly, in cybersecurity, any single suspicious activity is worth investigating. But the ability to correlate seemingly unrelated activities across multiple sources can make the difference between finding a suspicious activity and uncovering a full-scale breach.
In part 1 of this series, we shared how CrowdStrike Falcon Long Term Repository (Falcon LTR) allows CrowdStrike Falcon® platform customers to extend the life of their Falcon protection data for retrospective threat hunting, investigations and compliance. We got more specific in part 2, sharing three examples of how Falcon LTR can be used to hunt across historical Falcon protection data.
In the final post of this series, we’ll examine the benefits of correlating your Falcon telemetry with other security data using the combination of Falcon LTR and Falcon LogScale, CrowdStrike’s observability and log management module.
A Major Technological Leap Forward
The problem is not that threat hunters don’t want to correlate their security telemetry, it’s that historically the practice has been too expensive and laborious. Legacy security information and event management (SIEM) tools and traditional log management platforms simply make it cost-prohibitive to log everything. Searches stall under the weight of index-based architectures. As a result, bad actors slip through the cracks.
Falcon LTR is a major technological leap forward. Built using an index-free architecture and advanced compression technology that reduces the size of data up to 80x, Falcon LTR makes it feasible for you to store your Falcon protection data for as long as you want, at an economical cost.
On its own, this historical Falcon protection data can be highly valuable. You can do things like audit installed applications and search for file entropy with sub-second latency. And when a breach at a different company makes the news and your CISO asks if your company has been exposed, you have months of historical data to reference and search for vulnerabilities.
But as with our bank robbery example above, no single data source can tell the full story of a possible breach. This is where Falcon LogScale can add tremendous value.
Correlating Security Telemetry Using Falcon LogScale and Falcon LTR
Falcon LogScale is CrowdStrike’s observability and log management module. The technology disrupts legacy log management by allowing you to ingest and search your log and event data at petabyte scale — and for a fraction of the price of legacy platforms.
While Falcon LTR offers a cost-effective way to store your Falcon protection data, Falcon LogScale is perhaps the most affordable way to ingest your other security telemetry, including:
- Application events
- Windows events
- Okta (MFA) providers
- Browser telemetry
- IoT/OT/ICS data
- Network data (NDR)
- OSQuery data
When you’re ready to correlate data sources, Falcon LogScale makes it simple. Start by ingesting your Falcon protection data into Falcon LogScale. Next, you can ingest data from other sources into repositories following these instructions.
Once you’ve got data coming into a repository, you can configure connections to other repositories so data can be correlated. Figure 1 shows several repository connections that would allow us to correlate a variety of data sources, including the Falcon platform, Mimecast, Corelight and AWS VPC Flow data.
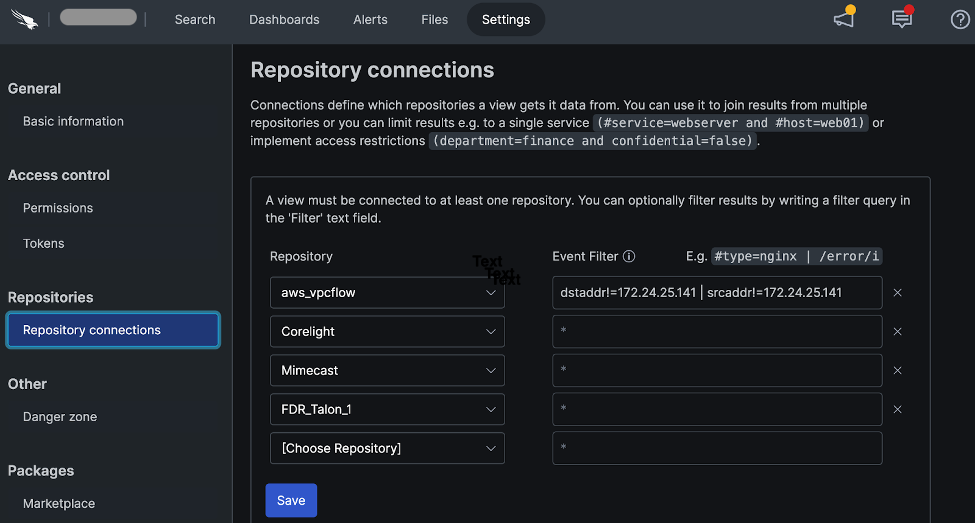 Figure 1. Falcon LogScale allows you to correlate and search across multiple data sources (click to enlarge)
Figure 1. Falcon LogScale allows you to correlate and search across multiple data sources (click to enlarge)Once you’ve correlated data sources, you can work with the data in different ways to learn how adversaries might be infiltrating your environment. In Figure 2, we see both network and endpoint data, and we have the ability to search across both data sources to look for potential indicators of compromise (IOCs) or carry out advanced threat hunting activities.
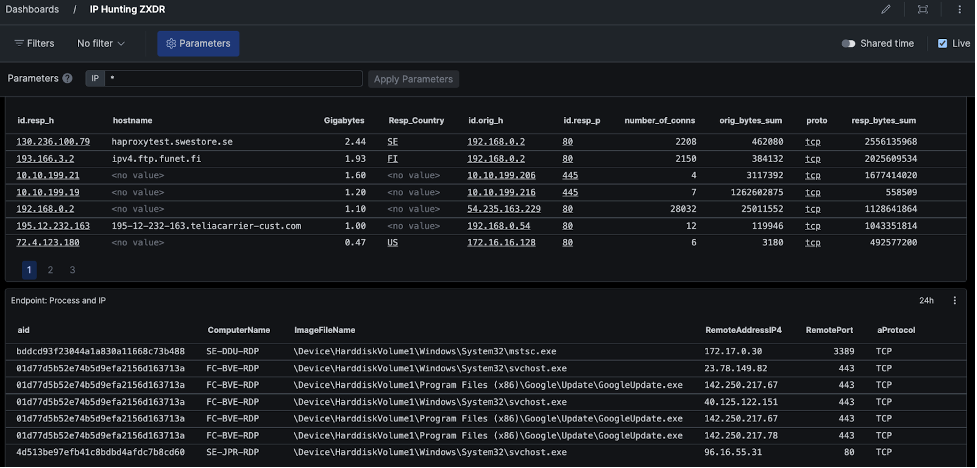 Figure 2. Falcon LogScale allows you to search for fields such as IPs across multiple data sources (click to enlarge)
Figure 2. Falcon LogScale allows you to search for fields such as IPs across multiple data sources (click to enlarge)See for Yourself
So, how would you put this functionality to work? A supply chain attack like SUNBURST requires security teams to take a long-term view of historical events to identify potential IOCs. Likewise, when a seemingly trusted and signed binary has been corrupted at the source, the ability to review historical data is required to reconcile when and how an adversary started their attack, as with Log4Shell.
But with limited data and visibility, many security teams struggle to patch and respond swiftly, putting their organizations at risk of a breach. That’s where the ability to easily correlate data sources and execute sub-second searches across that data can help you react and respond to potential threats faster.
In this 4-minute video, CrowdStrike Solution Architect John Smith investigates a suspicious user ID across Falcon protection data, Windows events and network events. Why is this cashier taking actions that don’t align with their job title? John demonstrates the breadth of context that can be achieved when correlating disparate datasets.
Get Started with Falcon LTR
As we’ve shown in this blog series, Falcon LTR is a powerful and versatile technology that solves real problems for customers. No longer must you endure the cost and complexity of creating data lakes to store your long-term security telemetry. Falcon LTR offers a seamless, end-to-end solution to migrate your Falcon protection data into Falcon LTR for cheap long-term storage and high-performance search and analysis.
When combined with Falcon LogScale, the two solutions become a force multiplier for threat hunts, allowing you to correlate your security telemetry for added context and improved visibility across your infrastructure — all from one user interface.
Additional Resources
- Read Part 1 and Part 2 in this Falcon LTR blog series.
- Learn about the Total Economic Impact™ of CrowdStrike Falcon LogScale.
- Watch The ReadOut: Falcon Long Term Repository.
- Contact us to request a demo of Falcon LTR and Falcon LogScale.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































