The term “threat hunting” is increasingly thrown around the cybersecurity industry as a catch-all for any proactive or human-lead defensive security measures. This is evidenced by the SANS 2020 Threat Hunting Survey, in which nearly half of respondents reported that they conduct threat hunting on an ad hoc basis.
Herein lies one of the most pervasive oxymorons of cybersecurity today: “part-time threat hunting.” The adversary doesn’t stop just because you’ve looked away from your screen. True threat hunting is highly specialized, highly structured and, most importantly, unrelenting. In today’s fight against a globally diffuse adversary, the enemy never sleeps — and hunters need to have eyes on glass 24/7/365.
In this two-part blog, we will look at why full-time threat hunting is the only way to effectively find and disrupt today’s adversaries. In this first part, we examine adversary breakout times and look at what it takes to find an adversary before they can entrench themself in your environment.
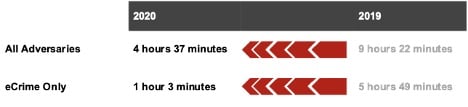 Average Breakout Time 2020 vs. 2019
Critically, Overwatch hunters see many intrusions where breakout time is measured in just minutes. In the past, rapid breakout times were commonly associated with targeted intrusion campaigns and state-sponsored adversaries using sophisticated or novel techniques. However, the element of speed is no longer solely the domain of sophisticated targeted adversaries. There has been a paradigm shift, with many of the shortest breakout times now observed in eCrime campaigns.
Of the hands-on intrusions in 2020 attributed to eCrime adversaries where breakout time was able to be derived, the average breakout time was just 1 hour 3
Average Breakout Time 2020 vs. 2019
Critically, Overwatch hunters see many intrusions where breakout time is measured in just minutes. In the past, rapid breakout times were commonly associated with targeted intrusion campaigns and state-sponsored adversaries using sophisticated or novel techniques. However, the element of speed is no longer solely the domain of sophisticated targeted adversaries. There has been a paradigm shift, with many of the shortest breakout times now observed in eCrime campaigns.
Of the hands-on intrusions in 2020 attributed to eCrime adversaries where breakout time was able to be derived, the average breakout time was just 1 hour 3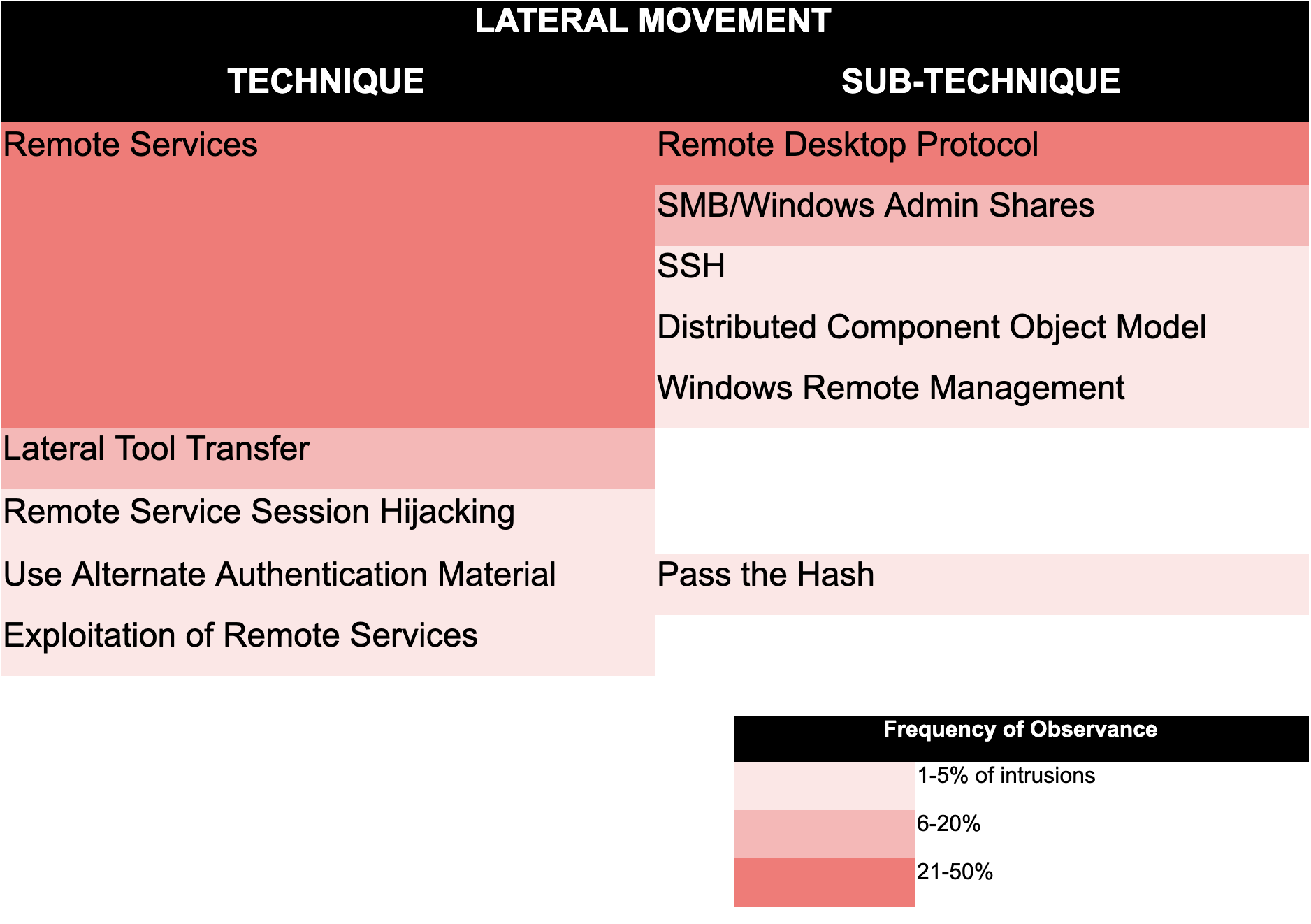 Most Commonly Seen Lateral Movement Techniques in 2021
To uncover activity that is designed to blend into the noise of daily operations, hunters need a clear understanding of what “normal” looks like in the given environment. They also need to be well versed in what to look for and be vigilant in looking for bursts of activity that fall outside of what is expected. In the case of these common lateral movement techniques, hunters may look for unusual access patterns, unexpected user log-ons, unusual file creation or transfer, or perhaps the same file being created across multiple systems within a short period. Crucially, hunters need to work in near real time to enrich any indicators of compromise with context to determine whether they warrant further action.
Most Commonly Seen Lateral Movement Techniques in 2021
To uncover activity that is designed to blend into the noise of daily operations, hunters need a clear understanding of what “normal” looks like in the given environment. They also need to be well versed in what to look for and be vigilant in looking for bursts of activity that fall outside of what is expected. In the case of these common lateral movement techniques, hunters may look for unusual access patterns, unexpected user log-ons, unusual file creation or transfer, or perhaps the same file being created across multiple systems within a short period. Crucially, hunters need to work in near real time to enrich any indicators of compromise with context to determine whether they warrant further action.
The Clock Is Ticking
The documented speed of today’s adversaries should persuade even the most skeptical observer of the inadequacy of ad hoc hunting. An important metric for gauging this speed is “breakout time,” which the CrowdStrike Falcon® OverWatch™ team uses to measure the time taken by an adversary to move laterally, from an initially compromised host to another host within the victim environment. Disrupting the adversary before breakout occurs is a critical factor in preventing an intrusion from becoming a serious breach. Once an adversary has established themselves on multiple hosts, often with redundant means of access, the defender’s mission becomes more complicated and potentially more expensive. In 2020, for intrusions where a breakout occurred, the average breakout time observed by OverWatch was just 4 hours 37 minutes. This is a significant reduction from 2019, when the average breakout time was roughly 9 hours. Average Breakout Time 2020 vs. 2019
Average Breakout Time 2020 vs. 2019minutes. Moreover, the OverWatch team found that in 44% of those intrusions, the adversary was able to move laterally to additional hosts in less than 30 minutes. This suggests that eCrime adversaries may be growing more capable at quickly moving between hosts on victim networks. In one such example from the second half of 2020, OverWatch uncovered a hands-on intrusion against a U.S.-based engineering firm following the successful compromise of a vulnerable SharePoint service. After gaining access, the adversary used PowerShell to conduct reconnaissance beneath the IIS worker process w3wp.exe and carried out a variety of other actions consistent with hands-on ransomware preparation. A short time later, the adversary, tracked by CrowdStrike Intelligence as ANTHROPOID SPIDER, pivoted and began moving laterally to numerous additional hosts using WMI in conjunction with valid credentials, before continuing their actions on objectives. The time between the initial SharePoint compromise and the first evidence of malicious activity on a secondary host was just 4 minutes 7 seconds. This example serves as a reminder that when it comes to disrupting adversary activity, minutes matter. Over the past few years, the eCrime ecosystem has become vast and interconnected. Ransomware-as-a-service (RaaS) operating models have grown rapidly, with numerous vendors marketing ransomware to affiliates that opportunistically deploy the malware. This proliferation of the RaaS marketplace, coupled with numerous highly publicized ransomware incidents, has led to a greater volume of ransomware campaigns than ever before. In turn, the substantial flow of funds back into eCrime syndicates continues to enable innovation that feeds the cycle of eCrime proliferation. Furthermore, over the last 18 months, CrowdStrike Intelligence observed the increasing importance of access brokers in the eCrime ecosystem. Access brokers are adversaries that gain backend access to organizations and sell this access to other threat actors. The specialization of functions is likely to also be contributing to more streamlined and faster intrusion campaigns. Breakout time is a defining parameter in the ongoing race between attackers and defenders. By
responding within the breakout time window, defenders are able to minimize the cost incurred and damage done by attackers. CrowdStrike continues to encourage security teams to strive to meet the metrics of the 1-10-60 rule: detecting threats within the first minute, understanding threats within 10 minutes, and responding within 60 minutes.
Breakout: How It Happens and What to Look For
The table below shows the most commonly seen lateral movement techniques observed by OverWatch threat hunters so far in 2021. What stands out here is that the most commonly seen techniques like the use of remote services with valid accounts or lateral tool transfer are not difficult techniques to execute but are potentially difficult to distinguish from legitimate activity. Most Commonly Seen Lateral Movement Techniques in 2021
Most Commonly Seen Lateral Movement Techniques in 2021Secure Your Environment — and Do It Fast
The cyber threat landscape continues to throw up new challenges for defenders. In the face of fast-moving adversaries and an ever-changing threat environment, organizations must not let their cyber defenses get lost in rhetoric and allow “threat hunting” to become another industry buzzword. Below are the dos and don’ts of securing your environment against a cohort of increasingly speedy adversaries.Do:
- Enlist hunters in the fight 24/7/365. Complement investments in technology-based defenses with continuous human-driven hunting to find and disrupt persistent and stealthy intrusions at whatever hour of day they may strike. Organizations may implement an in-house threat-hunting team, or they may look for a partner to leverage the expertise and around-the-clock coverage that outsourcing can offer.
- Practice basic security hygiene. It is hard to over-emphasize the importance of basic security hygiene in slowing down the adversary. Many of the most commonly used initial access and lateral movement techniques take advantage of weak passwords or poor access controls. Defenders can slow down the adversary (if not deter them entirely) by implementing and enforcing sound security policies including the use of multifactor authentication and employing strict user account management based on the principle of least privilege.
Don’t:
- Take your chances on “good-enough” security. Part-time hunting means only part-time protection. With adversaries operating around-the-clock, it is impossible to predict when they might strike. This fact, combined with ever-diminishing breakout times, means that there is a very real risk that an adversary could start and complete their mission during your hunting “downtime.”
- Let blindspots be your downfall. OverWatch hunters routinely see lateral movement originate from a host without CrowdStrike Falcon® sensor coverage. In fact, it is not unusual to see adversaries conduct reconnaissance early in an intrusion looking for potential blindspots that could become an initial foothold for their mission.
Additional Resources
- See how Falcon OverWatch won the race against a sophisticated eCrime adversary in this year’s MITRE Engenuity ATT&CK Evaluation.
- Learn more about Falcon OverWatch proactive managed threat hunting.
- Watch this video to see how Falcon OverWatch proactively hunts for threats in your environment.
- Learn more about the CrowdStrike Falcon® platform by visiting the product webpage.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)











































