Adversaries are taking aim at cloud environments, as evidenced by the 75% increase in cloud intrusions in 2023. Organizations are under growing pressure to ensure they have measures in place to effectively detect, investigate and respond to cloud-focused attacks.
Cloud detection and response (CDR) is uniquely challenging for SOC teams due to their limited visibility into the cloud control plane, resource configurations and application deployments. Gaining this visibility and critical context typically requires centralized knowledge and collaboration with engineering and DevSecOps teams.
To address these challenges, CrowdStrike Falcon® Cloud Security includes CDR capabilities powered by pre-runtime insights and runtime threat monitoring. These help teams protect against active cloud attacks and respond in a way that improves overall cloud security posture.
Deep Visibility into the Cloud Estate
Cloud infrastructure and resources are owned and operated by cloud, platform or DevOps teams. Therefore, this is where much of the knowledge related to the relationship among cloud resources, application services and data flows sits. As the cloud becomes a popular target for attackers, the SOC team’s lack of knowledge and visibility into their cloud environment becomes a significant blind spot, giving attackers the advantage of obscurity.
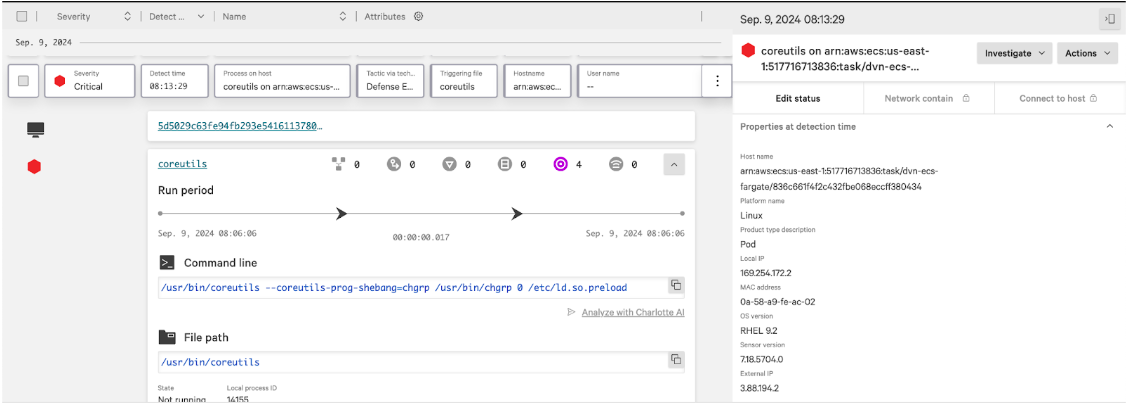
Figure 1. Cloud workload protection, built into Falcon Cloud Security, identifies and blocks threats in real time through CrowdStrike Threat Graph®, the industry’s most comprehensive set of endpoint and workload telemetry, threat intelligence and AI-powered analytics.
SOC teams need continuous access to security posture and metadata details related to cloud-native assets across cloud service providers (CSPs) in order to track their evolving cloud attack surface and activity. For example, cloud security posture tools can provide insight into risky cloud resources such as storage buckets configured with public access permissions. This helps security teams understand potential entry points for attackers, especially to sensitive or critical resources.
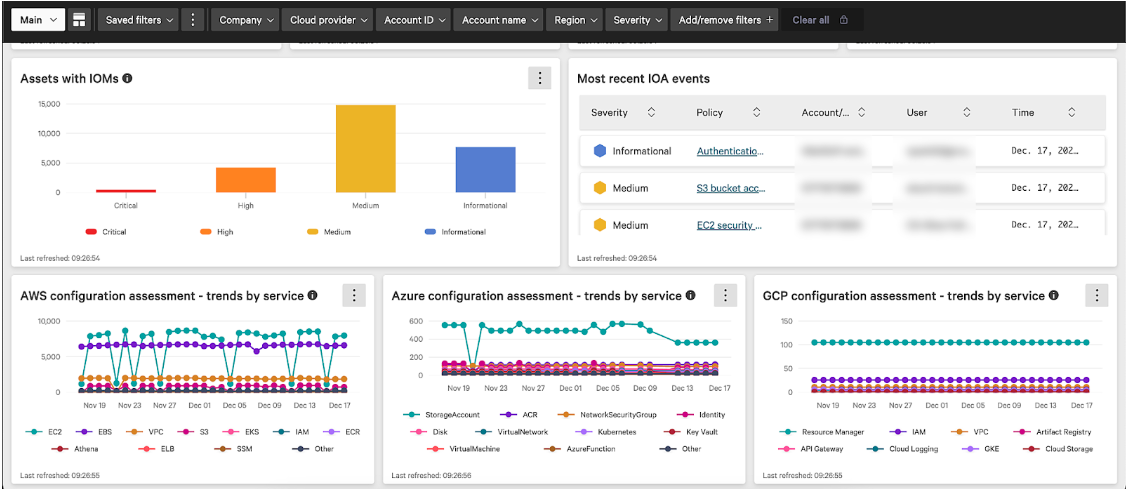
Figure 2. Falcon Cloud Security provides continuous insights into overall cloud security posture, which can be leveraged by SOC teams for visibility into their cloud attack surface.
Cloud Context Accelerates Investigations
The amount of time to respond to an attack is only getting shorter. The average eCrime breakout time — the time it takes an adversary to move laterally within a victim network after gaining access — is only 62 minutes, the CrowdStrike 2024 Global Threat Report revealed.
Cloud environments are vast. Compared to endpoint logs, there is a much larger scale and variety of logs to capture and sift through across layers of the cloud stack, yielding slower investigation times. Further, it’s difficult to decipher between legitimate and malicious activity in these dynamic cloud environments. Actions such as provisioning new resources or modifying IAM roles may look suspicious to a SOC team but could be legitimate engineering or DevOps activity.
Detecting advanced attacks on cloud environments in a timely manner requires correlating runtime workload anomalies with pre-runtime cloud posture insights for more contextualized investigations. Because cloud environments are interconnected — workloads interact with a variety of cloud resources such as databases and IAM roles — workload-only tools don’t see relevant relationships. This leads to alerts that lack context about how a compromised resource might affect the broader environment.
Cloud context is imperative. Today's adversaries target not just isolated systems but connected domains spanning endpoints, identities and cloud environments. These cross-domain attacks exploit fragmented security measures and use compromised credentials, valid tools and gaps between siloed systems to infiltrate, escalate and execute with speed and precision.
CrowdStrike commonly sees adversaries moving between the endpoint and identity planes, or from the cloud to an endpoint. One of the most proficient and prolific adversaries capable of cross-domain attacks is SCATTERED SPIDER (see the CrowdStrike 2024 Threat Hunting Report for an in-depth case study).
Quickly identifying such an attack relies on leveraging knowledge about SCATTERED SPIDER tactics, techniques and procedures (TTPs), combining this knowledge with telemetry from the control plane and correlating this information against detections from within the virtual machine. CrowdStrike Falcon® Adversary OverWatch™ plays a critical role in disrupting cross-domain attacks through 24/7 proactive threat hunting powered by AI, human expertise and CrowdStrike’s industry-leading adversary intelligence, providing unmatched protection against novel and evasive threats.
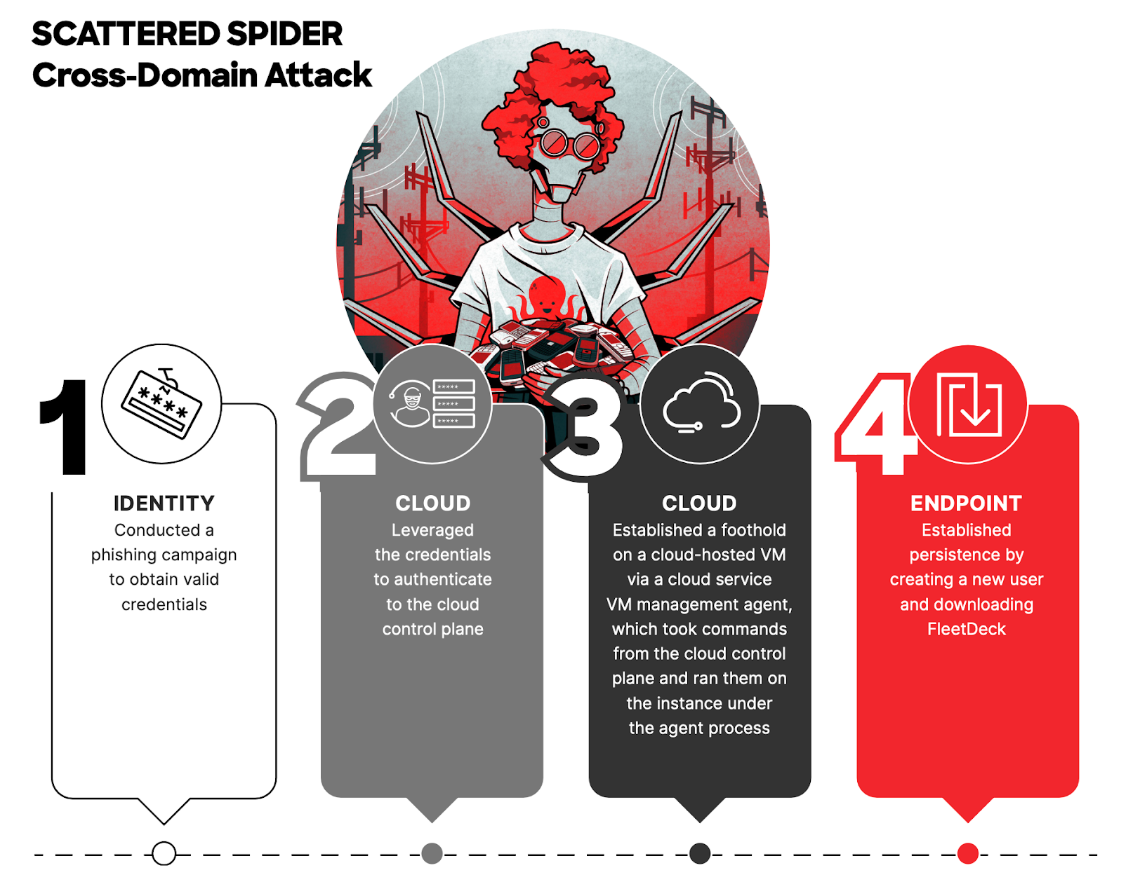
Figure 3. SCATTERED SPIDER cross-domain attack (Source: CrowdStrike 2024 Threat Hunting Report)
Coordinated Response Actions Improve Security Posture
SOC, engineering and DevSecOps teams must collaborate to effectively remediate cloud threats without disrupting operations. Response actions must be scalable to match the vast nature of cloud environments and use automated workflows to take actions such as isolating compromised resources, revoking permissions or applying patches across large-scale deployments. Since patching and infrastructure changes in cloud environments occur during the build phase, response actions following containment should feed back into shift-left practices, informing new security checks and guardrails that can improve overall cloud security posture.
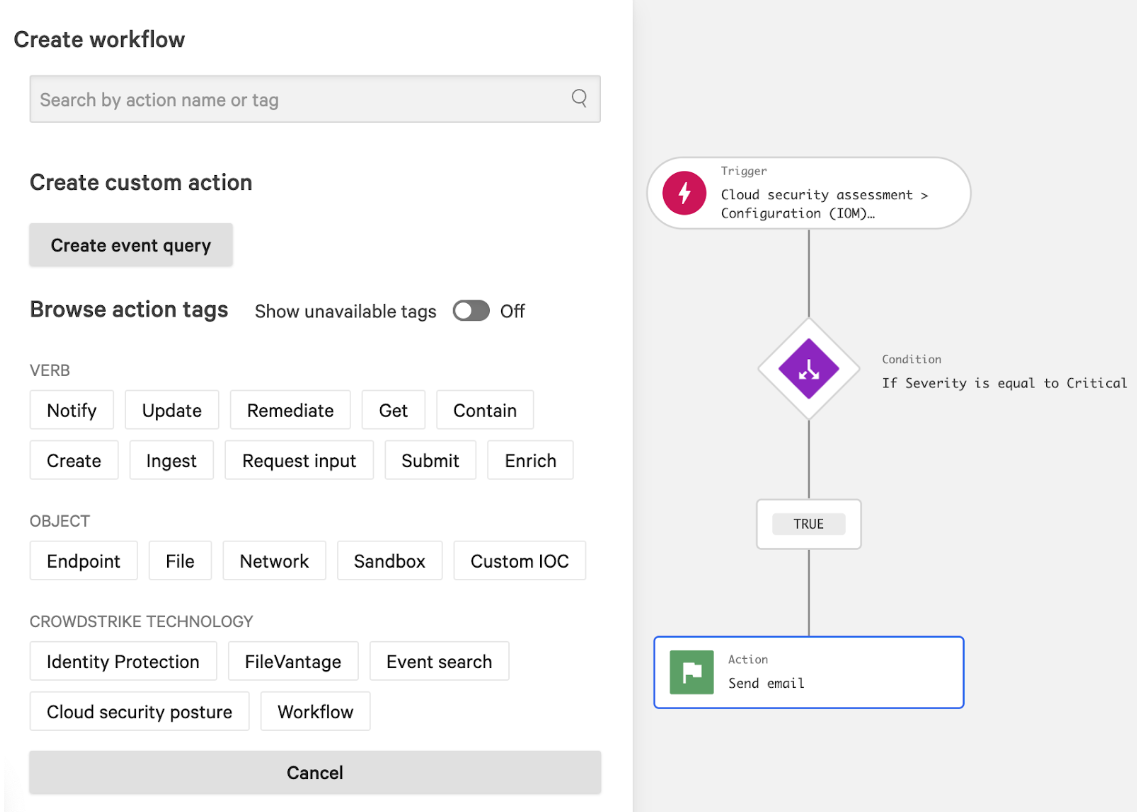
Figure 4. No-code playbooks are provided through CrowdStrike Falcon® Fusion SOAR, enabling automated remediation actions, with or without approval.
CrowdStrike Cloud Detection and Response
Many organizations are strategically pivoting their security approach to integrate CDR — in conjunction with expert incident response and breach recovery services — to address the unique challenges posed by cloud environments.
As a part of Falcon Cloud Security’s comprehensive cloud-native application protection platform (CNAPP), CrowdStrike offers the only CDR solution that unifies cloud security posture insights, real-time workload events and award-winning threat and adversary intelligence to help customers detect and respond to active cloud-based attacks. Teams can also lean on Falcon Adversary OverWatch 24/7 threat hunting and CrowdStrike’s expert services, such as incident response, to help stop cloud breaches.
Check out our website for more information on cloud detection and response with CrowdStrike.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)




















































